If you want to build a healthcare app dealing with protected health information (PHI), ensuring it complies with HIPAA regulations should be your top priority. Don’t know where to start with building HIPAA-compliant software? This guide is for you.
The global healthcare IT market is worth $329 billion this year and is expected to reach around 1,195.36 billion by 2033 with a CAGR of 17.9%. Similarly, the mhealth (mobile health) market size is expected to be worth around USD 187.7 Billion by 2033 from USD 78.6 Billion this year, growing at a CAGR of 11.5% during the forecast period from 2025 to 2033.
These stats indicate that there will be significant growth in areas like telemedicine, augmented and virtual reality, artificial intelligence, wearable technology, and the Internet of Medical Things – all areas poised to either improve patient health, aid in medical discoveries or reduce healthcare costs.
Do you want to build a healthcare app that could redefine the healthcare market by interacting with electronically protected health information (ePHI), like a hospital or healthcare startup? In that case, you must ensure HIPAA compliance.
However, what is HIPAA compliance, and why does it matter? This blog will briefly introduce HIPAA and how to develop HIPAA-compliant software. Let’s begin:
We respect your privacy. Your information is safe.
What is HIPAA Compliance?
HIPAA (Health Insurance Portability and Accountability Act) compliance of 1996 is a Federal law requiring covered entities and business associates to self-regulate their security practices to comply with specific standards. It outlines rules and regulations for protecting the privacy and security of individuals’ health information, also known as protected health information (PHI).
Here are a few reasons why your healthcare app should be HIPAA-compliant:
- Failure to be HIPAA-compliant may result in heavy penalties and brand reputation damage.
- Since HIPAA sets specific guidelines for handling and safeguarding PHI, it can prevent unauthorized access, use, or disclosure.
- By complying with HIPAA regulations, you can help to build trust with patients and demonstrate that you take their privacy seriously.
- Some healthcare providers and payers may only work with app developers that are HIPAA compliant. Becoming compliant can expand your potential customer base and increase revenue opportunities.
- A HIPAA-compliant app can save you from heavy penalties, build patient trust, and increase your potential customer base. That’s why your software must adhere to HIPAA compliance standards.
Which Healthcare Apps Should Comply With HIPAA Rules?
If you plan to develop healthcare software or a mobile healthcare app, you must pay attention to HIPAA. The essential questions to answer about whether your mHealth app or healthcare software needs to be HIPAA-compliant are:

What type of entity will use the application?
With HIPAA, the onus for compliance falls with the covered entity (healthcare provider, health plan, healthcare clearinghouse) or business associate (any associate who has access to PHI).
What type of data will the application use, share, or store?
Healthcare apps that plan to store, record, or share PHI will be subject to HIPAA rules during their use. Protected health information (PHI) and electronically protected health information (ePHI) refer to any identifiable data about the patient, including name, address, date of birth, SSN, device identifiers, email addresses, biometrics, lab or imaging results, medical history, and payment information.
Examples of healthcare and mHealth apps that need to be HIPAA compliant are:
- Telemedicine or secure/private messaging apps
- EHR apps
- Healthcare apps that collect data for, or communicate with, healthcare providers
- Medical records/lab results apps
- Patient monitoring apps or medication compliance apps, if connected with physicians
Healthcare software developers must know what HIPAA will require of the app regarding security controls and specific workflows, such as PHI removal (continue reading for more).
With the growth of the mobile marketplace and the number of wearable tracking devices, we see a boom in the use of mHealth apps – but not all of these apps need to be HIPAA compliant.
The Office of Civil Rights (OCR) stated that HIPAA is limited in regulating third-party health apps chosen by patients and not connected to or used by physicians – unless the app developer is a covered entity or business associate. Examples of mHealth apps that may be excluded from HIPAA include:
- Nutrition tracking or diet apps
- Personal health or mental health tracking
- Fitness or exercise apps
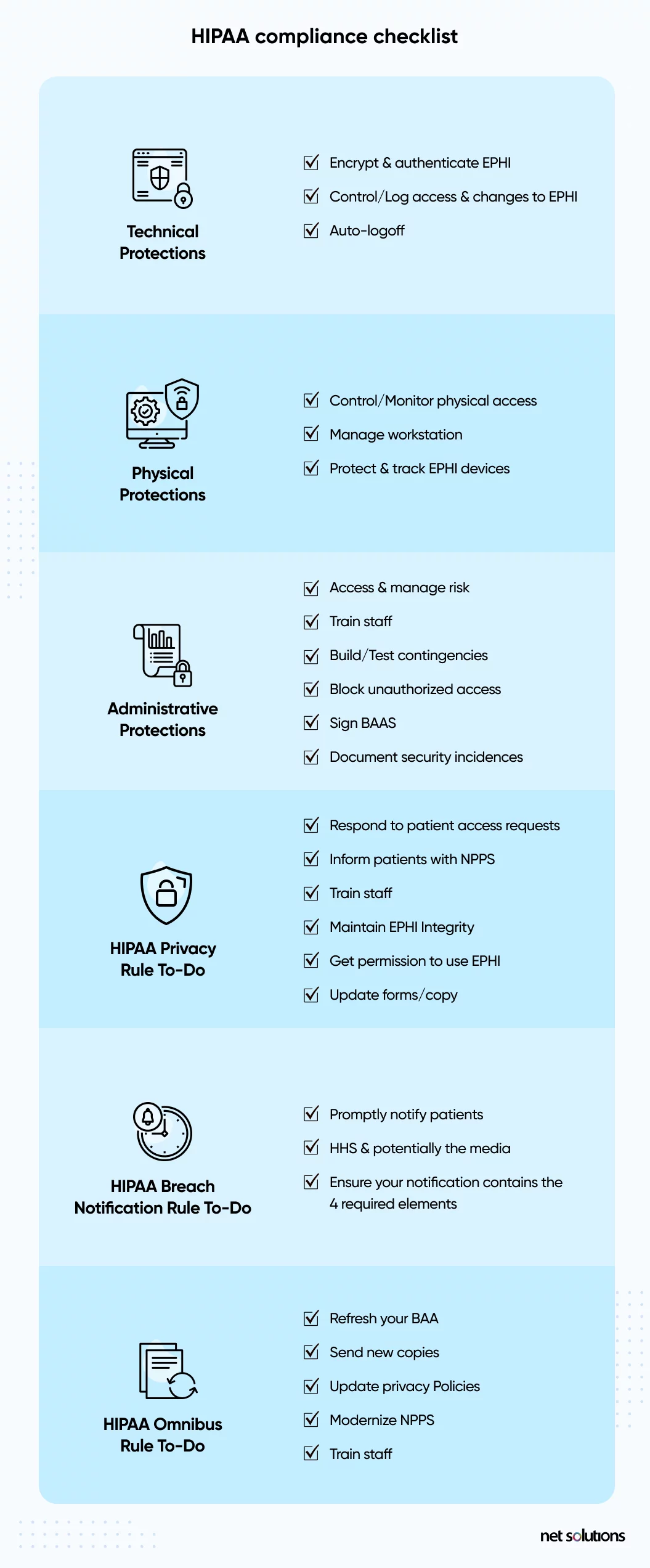
What Are The Requirements Of HIPAA Compliance?
HIPAA compliance involves meeting the requirements of HIPAA and its related rules, amendments, and related legislation. Generally speaking, HIPAA is both strict (with many rules and severe penalties) and vague (with liberty on how best to apply the rules).
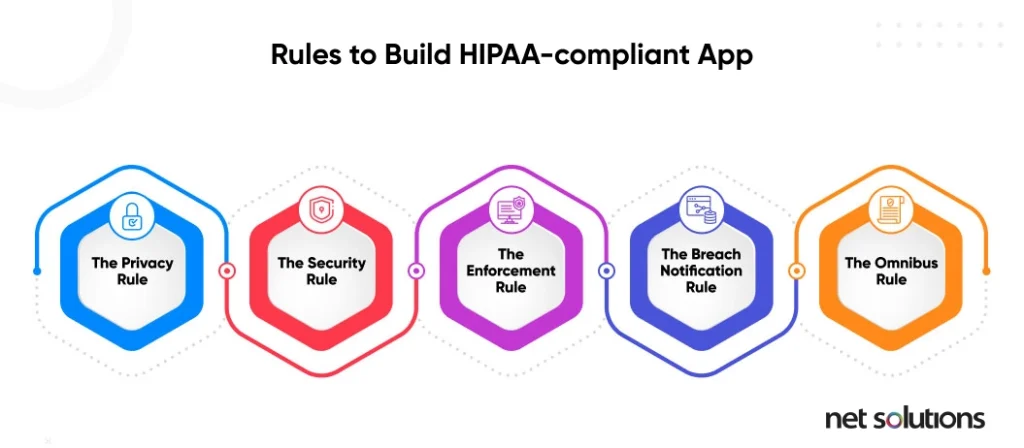
HIPAA defines 5 significant rules that all healthcare software applications must follow:
1. The HIPAA privacy rule
The Privacy Rule standards were designed to protect the use and disclosure of medical records and other PHI. The rule is meant to facilitate the flow of health data in a way that limits fraud and theft. The rule also gives patients certain rights over their health information, including the right to view, obtain a copy, and request corrections of their records.
2. The HIPAA security rule
The Security Rule sets standards to protect ePHI created, received, used, or maintained by a covered entity. The Security Rule requires that covered entities institute “appropriate administrative, physical and technical safeguards ensure the confidentiality, integrity, and security” of ePHI. Although HIPAA does not always state minimum or exact requirements, it is common to reference the NIST guide to implementing HIPAA (note-a revision is due).
3. The HIPAA enforcement rule
The Enforcement Rule establishes how the Department of Health and Human Services (HHS) enforces HIPAA, with regulators determining liability and calculating fines for non-compliance. Investigations typically stem from complaints or data breaches, but HHS retains the right to investigate without a trigger.
4. The breach notification rule
The Breach Notification Rule requires HIPAA-covered entities and their business associates to provide notification of a breach of unsecured PHI, both paper-based and electronic PHI. HHS further defines what qualifies as a breach based on the nature and extent of the PHI involved, the type of disclosure, whether the data was viewed, and the level of risk of exposure. In addition to other requirements, breaches that affect more than 500 residents must include a media notice.
5. The omnibus rule
The Omnibus Rule is the most recent addition to HIPAA, updated in 2013, and modifies several HIPAA Privacy, Security, and Enforcement Rules. The Omnibus Rule is more stringent, making it harder to avoid a breach notification, extending non-compliance liability to business associates, and instituting new privacy restrictions for using PHI.
HIPAA-compliant Software Examples
Here are some examples of HIPAA-compliant software:
1. HIPAA-compliant scheduling software

A HIPAA compliant scheduling software ensures that any appointment schedule involving the exchange of Protected Health Information (PHI) is secure and compliant with HIPAA regulations.
Here are some examples of HIPAA compliant scheduling software:
- Zocdoc: Zocdoc is a healthcare appointment scheduling software using which patients can find and book appointments with healthcare providers. The software is HIPAA-compliant as it has features like appointment reminders and a patient portal for secure communication.
- Mend: This telemedicine and patient engagement platform also include scheduling features. Mend is HIPAA compliant and has features like appointment reminders, virtual waiting rooms, and secure video conferencing.
- Luma Health: Luma Health is a HIPAA-compliant patient engagement platform with features like appointment reminders, waitlist management, and a patient portal for secure communication.
- PracticePanther: PracticePanther is a HIPAA-compliant practice management software with features like appointment reminders, task management, and document management.
- AdvancedMD: AdvancedMD is a cloud-based practice management and EHR platform which is HIPAA-compliant and equipped with features like appointment reminders, patient self-scheduling, and telemedicine capabilities.
2. HIPAA-compliant video software

With the rise of online consultations, video communication has become essential to healthcare. However, it also exposes you to cyberattacks and other threats.
The purpose of HIPAA-compliant video software is to ensure that any video communication involving the exchange of Protected Health Information (PHI) is secure and adheres to HIPAA regulations.
Here are some examples of HIPAA-compliant video software:
- Zoom for Healthcare: This popular video conferencing software offers a HIPAA-compliant version called Zoom for Healthcare – which lets healthcare providers securely connect with patients. Zoom for healthcare has many features that ensure the safety of PHI, such as encrypted messaging, screen sharing, and virtual waiting rooms.
- Doxy.me: Doxy.me is a HIPAA-compliant telemedicine platform that offers a secure video conferencing solution for healthcare providers. It has features like virtual waiting rooms, customizable intake forms, and appointment scheduling.
- GoToMeeting: This video conferencing software offers a HIPAA-compliant version called GoToMeeting Healthcare, which offers healthcare providers a secure platform for virtual appointments. GoToMeeting for healthcare includes screen sharing, recording, and virtual waiting rooms.
- Skype for Business: Skype for Business offers a HIPAA-compliant version called Skype for Business Online. It is a secure platform for virtual appointments, including features like screen sharing, recording, and virtual waiting rooms.
- Webex: Webex offers a HIPAA-compliant version called Webex Meetings Healthcare, a secure platform for virtual appointments. It includes screen sharing, recording, and virtual waiting room features.
3. HIPAA compliant accounting software
HIPAA-compliant accounting software ensures that any financial information involving the exchange of Protected Health Information (PHI) remains safe and adheres to HIPAA regulations.
Here are some examples of HIPAA-compliant accounting software:

- QuickBooks: This accounting software offers a HIPAA-compliant version called QuickBooks Online Advanced. It includes features such as encrypted data storage, audit trails, and role-based access controls to manage your financial information easily.
- NetSuite: NetSuite is a HIPAA-compliant cloud-based accounting software that includes financial information management features, data encryption, access controls, and audit trails. NetSuite also has other business processes like inventory management and customer relationship management.
- Sage Intacct: Sage Intacct is a HIPAA-compliant cloud-based accounting software for businesses of all sizes. It includes multi-entity management, automated workflows, and role-based access controls.
- Xero: This cloud-based accounting software offers a HIPAA-compliant version that provides a secure platform for managing financial information and includes features like bank reconciliation, expense tracking, and financial reporting.
- FreshBooks: FreshBooks is an accounting software for small businesses and self-employed professionals. It is HIPAA-compliant and has features like online invoicing, time tracking, and expense management.
6. HIPAA-compliant project management software
HIPAA-compliant project management software aims to ensure that any project-related information, including the exchange of Protected Health Information (PHI), is secure and compliant with HIPAA regulations.

Here are some examples of HIPAA-compliant project management software:
- Trello: Trello offers a HIPAA-compliant version for managing projects, including encryption, access controls, and audit trails.
- Asana: Asana is a HIPAA-compliant project management software that lets healthcare providers efficiently manage projects and secure PHI through access controls, encryption, and audit trails.
- Wrike: This project management software includes a HIPAA-compliant version equipped with features like encryption, access controls, and audit trails.
- Basecamp: Basecamp also includes a HIPAA-compliant version. Hence, healthcare providers can use them to manage PHI while ensuring it doesn’t fall into the wrong hands.
- Jira: This widely-used project management tool has a HIPAA-compliant version using which healthcare providers can better manage their projects while protecting PHI.
7. HIPAA-compliant CRM software

Here are some examples of HIPAA-compliant CRM software:
- Salesforce Health Cloud: Salesforce Health Cloud is a HIPAA CRM software designed specifically for healthcare providers. It has secure patient data management, encrypted messaging, and secure file sharing to protect PHI.
- Pipedrive: This popular CRM software includes a HIPAA-compliant version offering a secure platform for managing customer relationships with encryption, access controls, and audit trails.
- Zoho CRM: Zoho CRM also includes a HIPAA-compliant version for securely managing customer relationships.
- HubSpot CRM: HubSpot CRM has a HIPAA-compliant version that lets healthcare providers efficiently manage customer relationships while protecting PHI.
- Agile CRM: The HIPAA-compliant version of Agile CRM provides a secure platform for managing customer relationships.
8. HIPAA-compliant database software
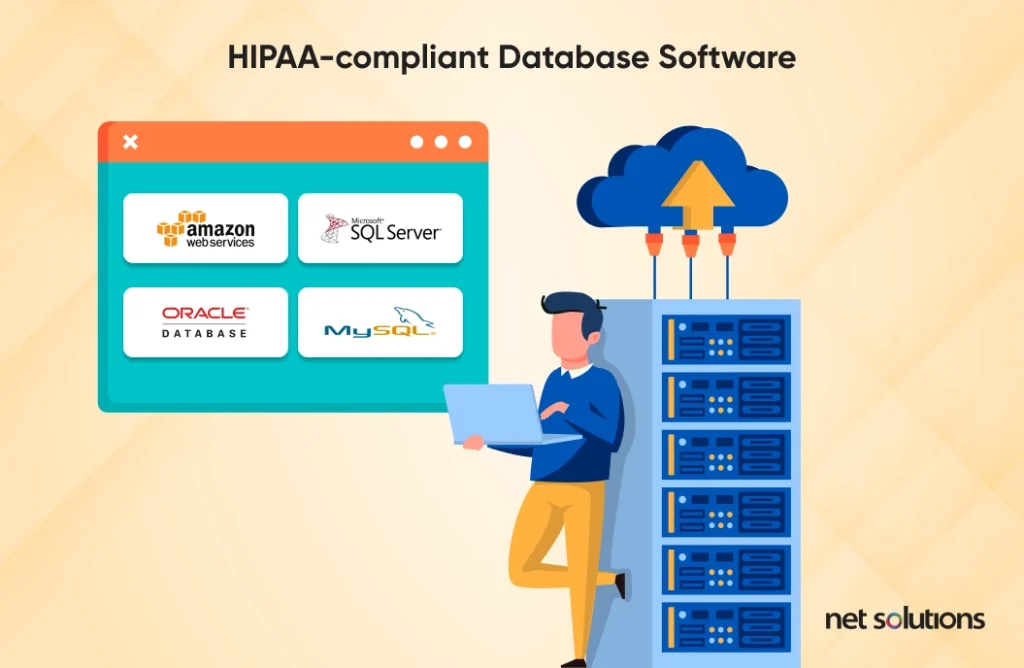
The purpose of HIPAA-compliant database software is to ensure that any database containing Protected Health Information (PHI) is secure and compliant with HIPAA regulations.
Some examples of HIPAA-compliant database software are:
- Amazon Web Services (AWS): AWS offers HIPAA-compliant database solutions like Amazon RDS (Relational Database Service) and Amazon DynamoDB.
- Microsoft SQL Server: Microsoft SQL Server offers a HIPAA-compliant version for managing databases that contain PHI.
- Oracle Database: Oracle Database also includes a HIPAA-compliant version that provides a secure platform for managing databases containing PHI.
- MySQL: MySQL has a HIPAA-compliant version to securely manage databases that contain PHI through encryption, access controls, and audit trails.
9. HIPAA-compliant software for therapists

Such software ensures that therapists don’t access patient health and treatment information, including the exchange of Protected Health Information (PHI) that’s not secure or compliant with HIPAA regulations.
Here are some examples of HIPAA-compliant software for therapists:
- SimplePractice: This HIPAA-compliant practice management software has features like secure messaging, appointment scheduling, and insurance billing features.
- TheraNest: TheraNest is a HIPAA-compliant practice management software designed specifically for therapists.
Compliance Beyond HIPAA
HIPAA is just one of a myriad of privacy and security laws and regulations that could potentially apply to new apps – be sure to consult a compliance lawyer to understand the requirements at the state, federal, global, and industry levels.
Want to know what laws apply to your mobile health app? The FDA released an interactive tool to help decide which laws apply in the US.
How to Ensure HIPAA Compliance for Healthcare Apps
What are the rules for developing HIPAA-compliant software and mHealth apps? The 5 HIPAA rules above outline the general expectations for data security and privacy, but there are many paths to implementing each rule.
It is important to note that HIPAA-compliant software does not guarantee compliance. The software users – the covered entities and business associates – ensure the software remains HIPAA compliant.
Risk assessment
Before starting on a healthcare app development, it is best first to understand your level of compliance (as above) and then to do a risk assessment of your organization, policies, and IT infrastructure to identify gaps in compliance. Look specifically at:
- What PHI will be collected, stored, or sent to other entities or associates
- Data management policies
- Employee training
- Data security practices and technologies
Next, as part of the new product development process, lay out specific policies and features to build into your healthcare app to make it HIPAA compliant.
Data storage & minimization
If data includes ePHI, it must be hosted on a server (on-premise or remote) with a signed Business Associate Agreement (BAA). Most large Cloud storage servers such as AWS, Google Cloud Platform, or Microsoft Azure are familiar with HIPAA.
Data security best practices are built around the concept of data minimization. Collect only the information necessary for the task – and nothing more. In health apps, this means collecting PHI only if it’s required.
Encryption
Encryption is one of the ways that covered entities and business associates can avoid a data breach notification. Healthcare software and mHealth apps can adhere to the HIPAA Security Rule, which requires that ePHI be encrypted with “an algorithmic process to transform data into a form in which there is a low probability of assigning meaning without use of a confidential process or key” (45 CFR 164.304 definition of encryption).
Data should be encrypted at rest (in all places, including Cloud backup) and in transit, with decryption tools stored on a device or at a separate location per NIST standards.
Data backup & disaster recovery
The HIPAA Security Rule requires robust backup and disaster recovery plans. A healthcare app must have the policy to back up PHI and other essential data. Data is stored in an offsite or mirrored Cloud facility to maintain uptime. Regularly monitor storage logs.
A disaster recovery plan describes what happens during a threat or attack.
Right to be forgotten: Data disposal
Although the term “right to be forgotten” is often associated with the EU GDPR (a different regulation), HIPAA requires adequate PHI disposal. In the case of ePHI, healthcare software must have a way to completely overwrite (clear) or purge (degauss) data or destroy (physically) the data or data device in all its forms (including backup).
Access controls
HIPAA requires that you not only store the least amount of information but implement controls around Access Management to limit access to PHI to only those authorized to see or use it. When the mHealth app store data between patients and physicians or between different users in a healthcare setting, these practices should apply.
Healthcare apps should include the following:
- Unique user identification (one login per user)
- Automatic log-off
- Emergency access to data (if ePHI needs to be accessed by a health provider, known as Emergency Mode)
- Encryption
- Strong authentication (see below)
- Access monitoring
As stated above, the app activity logs should be analyzed to identify unauthorized access or access attempts. Ideally, the healthcare software provides these kinds of alerts as a notification for IT teams to take rapid action.
Authentication
Robust user authentication is the root of strong security. There is growing evidence that passwords are no longer adequate and that even two-factor authentication leveraging SMS-based one-time passwords may be open to attack. However, HIPAA does not specify which kind of authentication be used, so more advanced security relies as much on the vague Security Rule as it does on avoiding the Breach Notification Rule.
The Zero Trust model for security is based upon the premise that there is no trust when it comes to access, assigning the least amount of privilege to users to allow them to access what they need and validating user accounts with as much trust as possible that people are who they say they are. The First Identity Online (FIDO) provides authentication standards that include 2FA (two-factor authentication), MFA (multi-factor authentication), or password-less (using biometrics, facial, voice, or security keys).
Integrity & Audit
HIPAA-compliant apps must implement technical and administrative safeguards to examine and track the activity in the systems storing and transmitting data to ensure integrity (that data is not unintentionally modified, corrupted, accessed, or removed) and to protect against (and detect) unauthorized access. This is done through:
- Authentication (as above)
- Transmission security (encryption in transit)
- Digital signature and verification (PGP, SSL)
- Healthcare app architecture (blockchain)
- Data safeguards (facility & device access controls for ePHI)
- System integrity, separating layers, and adding controls to each layer
- Push notification formatting should not contain PHI
Security policies, monitoring
Security technologies and policies still have a human element of concern – in almost every instance, human weakness can introduce the risk of cyber attack. Lost passwords, phishing attacks, emailing data, unhappy employees, or unpatched software can open the door to a data breach. You need to secure your app (lots of locks) and have an alarm system (monitoring) to know when an issue has occurred.
In software development, you want to be sure that your house (where you’re developing and using the software) is secure and build strong security into your app. Your app should provide the following:
- A minimum level of security for passwords
- 2FA or MFA or the option for hardware-backed security (passwordless)
- Automatic log-off
- Intrusion detection
Employees need to be trained in the above elements to build them into a healthcare app and abide by them internally if a covered entity or business associate.
Remediation plan
In a data breach, a plan must be in place to identify who was affected and notify those users of a breach.
How can Net Solutions Help You in Creating a HIPAA-Compliant App?
Protecting patient data and adhering to industry regulations are top priorities for any healthcare services provider as they build trust, prevent costly breaches, and avoid expensive lawsuits. Hence, ensuring that the app you’re building complies with HIPAA and other global regulations is essential.
As a leading healthcare software development company, we have an in-depth understanding of global privacy regulations, user experience design and strategizing to build secure and robust healthcare software solutions.
Contact us if you have a transformative healthcare app idea in mind. Our experienced team at Net Solutions can help you consult, design, and build a product on it.
Frequently Asked Questions
PHI refers to any identifiable data about the patient, including name, address, date of birth, SSN, device identifiers, email addresses, biometrics, lab or imaging results, medical history, and payment information. When data is electronic, we refer to ePHI.
A business associate is any person or entity performing functions for a covered entity that involves PHI’s use (holding or transmission).
Microsoft offers HIPAA-compliant services and solutions for healthcare organizations that must store, process, and transmit protected health information (PHI) in compliance with the Health Insurance Portability and Accountability Act (HIPAA).
Gmail is not HIPAA-compliant for the following reasons:
- Gmail does not provide the technical safeguards to protect PHI’s confidentiality, integrity, and availability. For example, Gmail does not offer end-to-end encryption, meaning unauthorized parties can intercept and access messages.
- Gmail’s servers are not located in HIPAA-compliant data centers, which means that PHI may be at risk of unauthorized access or disclosure.
- Gmail does not sign a Business Associate Agreement (BAA) with covered entities or business associates. BAA is a legal contract that outlines each party’s responsibilities for protecting PHI per HIPAA regulations. Without this agreement, you can’t hold Gmail accountable for any breaches or non-compliance issues that may occur.





