Summary: The growth in digital healthcare has increased the need for ecosystems catering to patient comfort and security. Data security concerns become the foremost priority given the sensitivity of health records and the systems needed for impeccably streamlined information management. Security breaches can destroy trust and endanger health & lives, and data is the backbone of modern cloud healthcare. Organizations need a comprehensive, multi-pronged approach to ensure security and fight growing threats from cyber-crime. Compliance standards also need to be considered while formulating data protection policies. Here’s a glimpse of the danger to healthcare data, prevalent compliance norms, and solutions for data protection.
The healthcare industry remains the most highly targeted industry for cyber attack, due in part to the high value of protected health information (PHI). The average cost of a healthcare data breach reached the astonishing level of $9.23 million in 2021, with 714 healthcare data breaches of 500 or more records being reported. IT security is an aspect to be given immense attention and one cannot underestimate the importance of data security in healthcare.
While many assume these attacks to focus only on large healthcare networks and hospitals, cyber criminals do not discriminate in their tactics, and in fact small healthcare practices are more vulnerable to cyber-attacks. For practices with five or fewer providers, 51% of data breaches were caused by human error and yet nearly half of all small practices say they spend no more than two hours of security training in the entire year.
Today’s medical practices and chains are not immune to the demands of the consumerization of IT. Today’s patients expect a seamless experience with their healthcare providers, from online booking and reminders to secure communication, virtual appointments, and online intake forms. With the advent of new practice management and patient experience software come many advantages, the flip side is increased risk for those practices not being proactive about healthcare data security best practices.
In this guide, learn about the latest threats to healthcare data, common healthcare data security challenges, and some healthcare cybersecurity best practices.

We respect your privacy. Your information is safe.
Top Threats to Healthcare Data
What is the biggest threat to the security of healthcare data? IT systems. But to break that down further, the top healthcare data security challenges are:

1. Ransomware
Ransomware is a type of malware in which a cyber criminal exfiltrates (removes) and/or encrypts (locks) access to the data or system until a ransom is paid.
2. Phishing
Phishing is a social engineering attack that is most commonly perpetuated over email, though it can also be sent via text message. A phishing attack is designed to get the end user to provide their credentials, download malware, or to reveal other sensitive information that could be used to gain initial access to a healthcare system. This is the most common point of entry for any attack.
3. Unauthorized access or disclosure
It is not only criminal actors who attack data, putting it at risk. Many times data is either inadvertently or maliciously exposed by someone in the healthcare environment, either saving data to a thumb drive, sharing it over email, or not properly disposing of data in physical (paper) or electronic form (hard drive). There are also compliance failures associated with a failure to log out of a healthcare system that is used in a public environment.
4. DDoS attacks
Dedicated Denial of Service (DDos) attacks send high volumes of traffic that can force a healthcare server offline, also often for ransom but without the same risk of data exfiltration.
5. Mobile devices
There are more devices being used in healthcare than ever before, both at the in-patient level (such as tablets and mobile devices for charting & communication) and to communicate with patients. Ensure that any software being used within clinic or with patients meet the most stringent compliance standards.
Healthcare Compliance: HIPAA and Beyond
The healthcare industry is most directly impacted by HIPAA, the Health Insurance Portability and Accountability Act, but compliance in healthcare does not end there.
1. HIPAA
HIPAA is actually a set of several rules, most importantly the HIPAA Security Rule and the HIPAA Privacy Rule lays out very specific guidelines for healthcare data privacy, confidentiality and security of health information, including the need for technical, physical and administrative safeguards to protect data against breach:
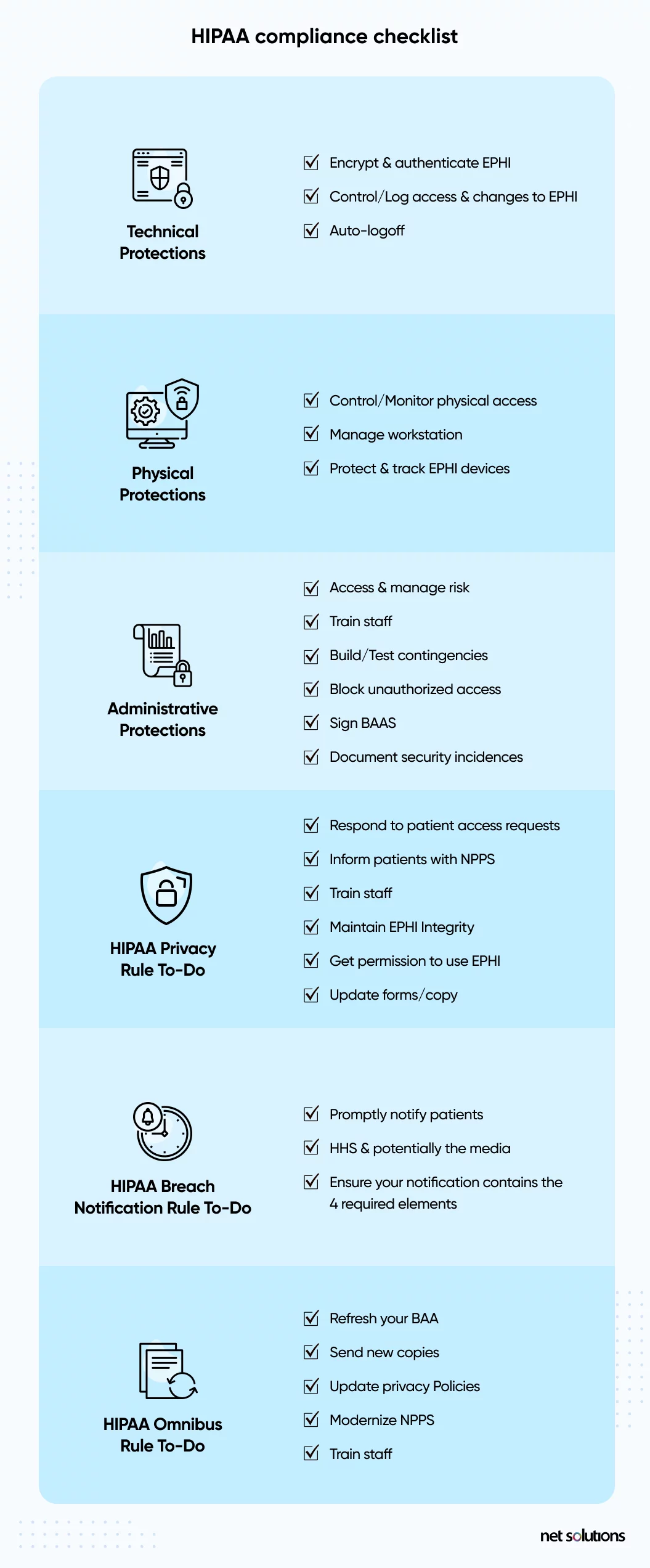
When it comes to the technical protections, healthcare organizations must have the basics in place to encrypt data, control access, set up authentication protocols, and audit all activity.
HIPAA is further supported by the HIPAA Safe Harbor Bill, which amends the HITECH Act, and the NIST framework for HIPAA implementation.

We respect your privacy. Your information is safe.
2. State Laws: CCPA & Others
The California Privacy Rights Act (2023) adds to the recent California Consumer Privacy Act (2020), among the most stringent healthcare data privacy regulations at the State level in the US, designed to protect the data of residents of California – which could impact other States. Following suit, similar regulations have emerged in Virginia and Colorado.
3. EO 14028
Executive Order 14028 is a directive by the current administration to improve the Nation’s cybersecurity, but with trickle down impact on other regulated industries, including healthcare. The EO requires that organizations move toward a Zero Trust architecture and sets forth stringent standards for access and phishing-resistant authentication.
4. GDRP
The EU’s General Data Protection Regulation (GDPR) impacts the data of any EU subject, which has global implications. The GDPR is one of the most stringent healthcare data security standards, requiring data protection by design and default, placing limits on data collection, and introducing the ‘right to be forgotten.’ In addition to HIPAA, GDPR has one of the most costly fines for a healthcare data breach.
5. Others
Depending on what aspect of healthcare an organization is involved in, there could be many more regulations to be aware of. For example, the Electronic Prescription for Controlled Substances (EPCS) requires that devices being used for electronic prescription have two-factor authentication compliant with FIPS 140-2 Federal standards.
10 Steps to Implement Healthcare Data Security
How can healthcare data be protected? To create a healthcare data security plan, it’s important to take lessons from compliance standards (particularly HIPAA) and ensure each step taken is in line with those healthcare data security standards.
Step 1: Educate Healthcare Staff
One of the top ways to improve healthcare security is to expand the amount of training staff receive on common weak points such as phishing attacks or other social engineering tactics or other common breach points such as sending data by email or failing to log out of systems. There are many online and free courses available.
If staff training is not enough, this could be a red flag that current healthcare software systems are creating workflow challenges that increase the time it takes to provide or support care. In these cases, an expert in healthcare software may be able to help.
Step 2: Implement Physical Security in healthcare
In order to comply with HIPAA, healthcare organizations need to implement facility access controls and protections to limit access to areas where PHI may be stored, processed, or accessed.

We respect your privacy. Your information is safe.
Step 3: Control Healthcare Secure Data Access (Control Data Accessibility)
In almost every healthcare security standard there is the requirement to control access to data and applications. Although all access should be protected, the most privileged levels of access (administrative level) require the greatest level of protections.
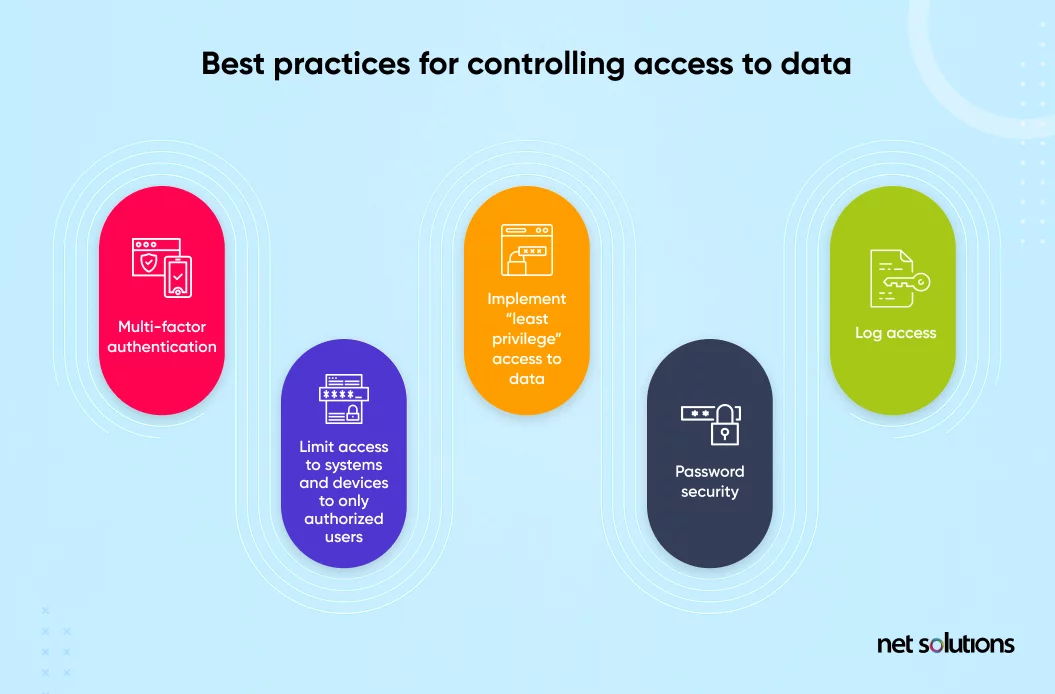
- Strengthen user authentication to include 2-factor or multi-factor authentication (MFA)
- Consider using a phishing-resistant hardware key and/or implementing the strongest “identity” proof that includes biometrics (facial recognition, eye scanning, fingerprint)
- Limit access to systems and devices to only authorized users
- Implement “least privilege” access to data or features within systems, so not all users can see the same depth of information or can control the system (such as prescription writing, deleting information).
- Heighten password security
- Log access
Step 4: Implement Data Controls
Beyond access to data, controls should include monitoring for risky behaviors such as attempts to exfiltrate data, sending data by email, copying to external drives, or printing information that should not be printed.
Step 5: Log Files
HIPAA regulations require that covered entities and their business partners keep six years of log data, gathering event logs and records from servers, devices, and workstations. Correct logging is one of the areas where smaller practices often have healthcare data security challenges.
Step 6: Encryption
Encryption remains one of the ways that covered entities and business associates can potentially avoid a data breach notification. Healthcare software and mHealth apps can adhere to the HIPAA Security Rule which requires that ePHI be encrypted with “an algorithmic process to transform data into a form in which there is a low probability of assigning meaning without use of a confidential process or key” (45 CFR 164.304 definition of encryption).
Data should be encrypted at-rest (in all places, including Cloud back-up) and in-transit, with decryption tools stored on a device or at a separate location per NIST standards.
Step 7: Secure Wireless Networks & Messaging Systems
Ensure wireless network infrastructure as well as internal and external messaging systems meet the minimum compliance requirements. Many mistakes are often made with the insecure use of text messaging or device messaging systems such as WhatsApp, applications which do not meet minimums of HIPAA.
Step 8: Secure the Endpoint
The importance of data security in healthcare extends to every place that data could be used or accessed – including the endpoint. The endpoint refers to any device that could access, process or store PHI, including mobile devices, tablets, laptops, desktop devices, or connected devices such as printers.
Endpoint security is the process of securing the devices that are being used in the medical practice in any way, including potentially personally-owned devices.
- Choose an endpoint protection platform (EPP) or mobile device management (MDM) system to specifically manage all devices, settings and configurations, regardless of device ownership
- Choose endpoint security platforms to add visibility, security, and patch management
- Enforce the use of strong password or PIN and step-up 2FA or MFA access to secure systems or data
- Enable the ability to remotely wipe & lock a lost or stolen device
- Educating users on appropriate use of mobile devices
- Ensured that secured applications can be installed
- For company-owned devices used in clinic, restrict the applications that can be installed on the device to reduce the risk of malware
- Keep devices and software up to date
- Ensure any connected devices (e.g. printers, fax machines) are kept up to date
Step 9: Conduct Regular Risk Assessments
Regular risk assessments are critical to uncovering potential risks to the privacy and security of protected health information – after all, this is information you want to know about before it leads to a costly data breach. There are many companies, and even some software tools, to help audiet healthcare security preparedness.
In order to meet the specific requirements of HIPAA’s Omnibus Rule, ensure that such risk assessments extend to business associates or software suppliers (this includes the use of any third-party service such as Google Doc or any other use or storage of PHI).
Step 10: Backup Data
To avoid the potential costly risk of ransomware and, just as importantly, to protect the continued ability to support patient care with accurate data, ensure data integrity with back-up to a secure, offsite location. Daily back-ups are an essential aspect of emergency preparedness for any practice size.
Frequently Asked Questions
Ransomware is the biggest healthcare data security threat at present. It is because many organizations feel they’re equipped to handle such attacks, but they lack the means. There are also threats like increased access to sensitive data, lack of secure logins, identity theft, and account takeover attacks that healthcare service providers shouldn’t overlook.
- Properly train your healthcare staff on the importance of data security.
- Restrict access based on roles and responsibilities.
- Monitor data usage and implement data usage controls.
- Use encryption mechanism to add an extra layer of security.
- Conduct regular security audits to ensure your patients’ data is safe.
Electronic health records are sensitive and more comprehensive than any other type of record. Also, someone’s health information is precious. Their whole life depends on it. Hence, it is a valuable asset for cyber-criminals.



