Enterprises and small and medium-sized businesses (SMBs) have been embracing the cloud for its flexibility and as a platform for growth. According to the latest research, SMBs using the cloud grow 26% faster and are 21% more profitable, while enterprises praise the cloud for its resiliency, agility, flexibility, and scalability. Yet cloud security concerns continue to hold organizations back from fully embracing the cloud – hesitation which often reduces cloud ROI.
In this post, we will examine the common areas of cloud security concerns as well as the cloud security frameworks that can help you support the complex demands of a hybrid workforce and changing consumer expectations.
Cloud Adoption in 2021
The cloud refers to any computing service available on-demand over the Internet. The cloud can be public (owned and operated by a third party), private (used exclusively by one business, hosted on-site or at a third-party), or hybrid, which allows data and apps to move between the two for the greatest flexibility. Business cloud computing services can be broken down in many ways, with the main three being:
- Infrastructure as a Service (IaaS) – Servers, storage, networking
- Platform as a Service (PaaS) – An environment to develop, manage, host applications
- Software as a Service (SaaS) – Online software application
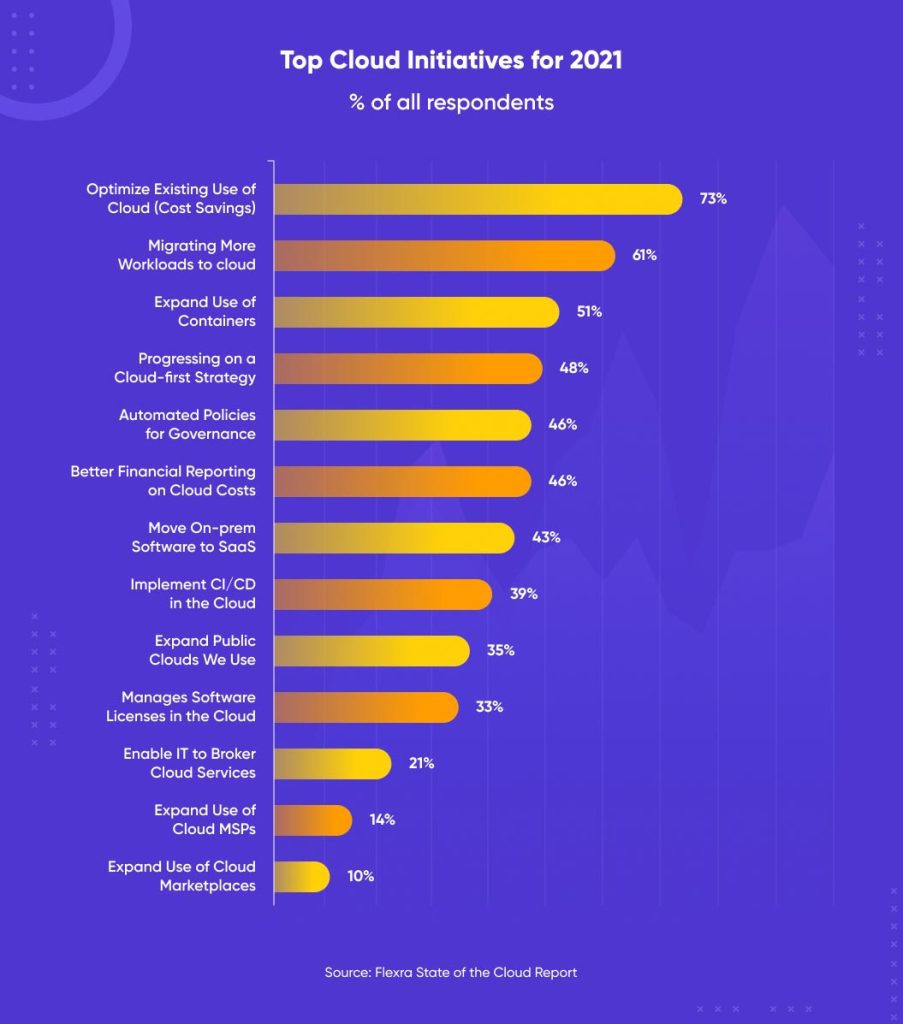
In the past 12 months, business initiatives have focused on migrating more workloads to the cloud toward a “cloud-first” strategy which prioritizes cloud services over infrastructure investment. According to Gartner research, global spending on public cloud services is forecasted to grow 23.1% in 2021 to a total of $332.3 billion, driven in part by the accelerated digital transformation brought about by COVID-19.
While cloud use has continued to grow, only 20-40% of enterprise workloads were shifted to the cloud prior to the COVID-19 pandemic – in part due to security concerns. 96% of cybersecurity professionals are at least moderately concerned about public cloud security, with 73% saying their security readiness is above or below average. A lack of cybersecurity staff and a lack of security awareness remain the top barriers to improvement.
The volume of public cloud utilization is growing rapidly, so that inevitably leads to a greater body of sensitive stuff that is potentially at risk. Jay Heiser,
VP and cloud security lead at Gartner, Inc.
Cloud Security Challenges
When it comes to cloud computing security, the top concerns are cyber attack (and data breach) as well as regulatory compliance. Broken down further, the biggest concerns revolve around visibility, access controls, and misconfigurations. In this article, we break down these challenges and offer some cloud security best practices to help you migrate to the cloud with confidence.
Cloud security is a dynamic partnership between businesses and cloud-service providers. Tweet This
Cloud Provider Challenges
A common misconception is that you can “offload” security requirements to your cloud provider. While cloud service providers (CSPs) can improve your security posture by investing in shared infrastructure you may not otherwise have access to, cloud security remains a shared responsibility. It is important to understand how your cloud provider will protect your data and to have regular visibility into the privacy and security measures being adopted by cloud service providers.
1. Control Over Cloud Data
1. 1. Access to Cloud Data and Applications
Organizations do not have the same control over infrastructure in the public cloud as they do for on-premise solutions. As public-cloud infrastructure is available over the Internet, access controls are important to keep personally identifiable information (PII) and intellectual property (IP) safe. Best practices would include switching to two-factor authentication (2FA) or multi-factor authentication (MFA), ideally with a key or token that is unique to the person, and with policies that restrict user access to only those who need it. Double check that your cloud provider’s internal practices are equally stringent around physical security and user access.
1.2. Vendor Lock-In for Security Features
Vendor lock-in is a common fear, with businesses wary of switching costs or dependencies on specific implementations or features. Although each CSP may do things a little bit differently, generally speaking most cloud services are pay-as-you-go, with options to shut down and export your data into alternate options quite easily. From a shared responsibility perspective, the onus here is on businesses to ensure data remains in a portable option, rather than a format that increases the risk of lock-in. A hybrid and/or multi-cloud approach also gives businesses the option to decrease lock-in risk.
2. Compliance and Regulations
Rapidly changing industry, state, federal and global regulations, standards, and frameworks on data and privacy are a concern for businesses of all sizes. Strict regulations such as the EU GDPR and CCPA as well as emerging regulations such as the EO on Improving the Nation’s Cybersecurity Act, place strict standards on where and how data is stored, accessed, shared, and deleted by organizations and third-party cloud providers, as well as provisions on data breach notification. Organizations must review their contracts with cloud service providers to understand and comply with these overlapping laws and frameworks. Large cloud service providers typically comply with the highest security frameworks (such as NIST) and offer localized cloud service centers.
3. Cloud-Native Breaches
Cloud-native breaches leverage the cloud (and any vulnerabilities there) to land the attack, expand laterally, and compromise data (exfiltrate or lock down with ransomware). One of the top areas of vulnerability is misconfiguration (addressed below) and visibility, with 93% of cloud applications not enterprise-ready and extensive SaaS sprawl, creating an attack surface that often goes unchecked (particularly with decentralized purchasing or the use of free, open-source SaaS against policies).
Organizational Challenges
4. Insider Threats
Insider threats relate to the accidental or malicious compromise of data or systems by employees or third-parties with authorized access. 50% of organizations are not sure they can detect insider threats stemming from the cloud. One of the best ways to mitigate insider threats is to improve your access controls: limiting data and system access to only those who need it, at the right admin level, with strong authentication protocols and regular auditing. Supporting that, employee training on data security practices can go a long way to avoiding simple mistakes (such as emailing copies of spreadsheets) or common phishing techniques that can introduce risk. To minimize the risk of malicious insiders, ensure your exit protocols promptly restrict user access.
5. Insecure Application & Configurations
According to a recent report from McAfee, 99% of IaaS misconfigurations go unnoticed, one of the most common entry points for cloud-native breaches. As these misconfigurations are client-side, this underscores the need for shared responsibility and to consider cloud-native tools such as data loss prevention (DLP) that can help audit configurations to ensure data is being stored and protected against breach and non-compliance.
6. Lack of Personnel Experienced in Cloud Security Measures
U.S. talent scarcity, IT skills in particular, has tripled within the past decade, with 69% of employers struggling to find the right people for their needs. This skill shortage is particularly acute in IT security and cloud security. Smart outsourcing can align your organization with the right people, skills, and services to help audit and support your cloud-first strategy, from understanding what applications and services are best for the cloud, to supporting your cloud migration, to implementing the right framework to keep you secure.
Learn more about our top-notch software outsourcing services.
External Challenges
7. DDoS and Denial of Service (DoS) Attacks
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks can prevent users from accessing cloud-based data and applications by making the service unavailable – often by flooding bandwidth or disrupting resources. There are various options to reduce the threat of DDoS and DoS attacks including blackhole routing, rate limiting, IP blocking, firewalls, or protection services. We also recommend building in redundancy against these kinds of attacks and malware with backups and load balancing.
8. Account Hijacking
61% of data breaches in the past year involved credentials, with this increasing as the number of cloud services (and access points) increase. Reiterating the need for shared responsibility, this comes right back to strong access controls and training on phishing and social engineering schemes that could compromise access. To avoid the threat of credential-based attacks for your most sensitive data and systems, adopt 2FA or MFA that relies on FIDO Authentication.
9. API Attacks
An API attack is the hostile use of an API to gain leverage to web applications and data. While the concept of being “open” is central to digital transformation, API security testing can often be overlooked in the application testing phase. A recent survey indicated that 91% of respondents had a security incident in production APIs in the past year. As with other areas of concern, you can reduce the threat of API attacks with strong access controls (tokens), encryption, and API traffic monitoring tools.
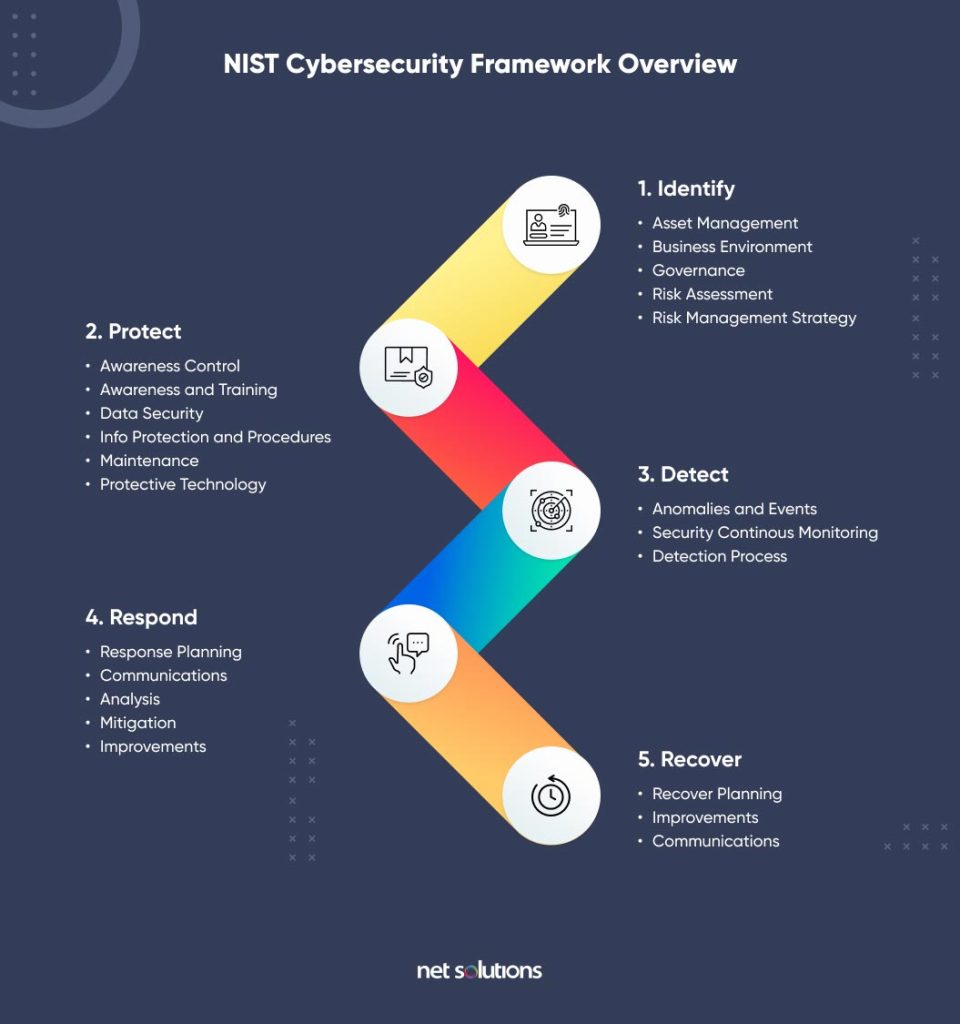
Cloud Security Framework: A Checklist
If you are ready to take the next steps on improving your cloud security, there are various frameworks that can help you institute the appropriate controls on all areas and types of cloud technology. Common frameworks include the Cloud Security Alliance Cloud Controls Matrix (CCM) or the NIST Cybersecurity Framework as it applies to the cloud, including SP 800-146 and SP 800-145, namely:
Cloud Security Challenges: The Takeaway
Cloud security is possible as long as you understand your shared responsibility in understanding risk and staying on top of the ongoing needs to protect, detect, and respond to the evolving threat landscape using some of the tips above. Whether you’re a growing startup or an enterprise with complex needs, we can help with your cloud-first strategy – building digital products and migrating your systems to the cloud with security considerations built into every step.





