Security is a serious consideration for any eCommerce platform. It can either make or break customers’ trust in your brand. Read on to learn what potential security threats can your ecommerce website face and what measures you can take to safeguard it.
eCommerce businesses have grown exponentially in the past several years, with the global eCommerce market expected to see sales of over $5.545 trillion in 2022. Fueled by the adoption of mobile technologies, the rise in “borderless” eCommerce, improved payment processing and changing buyer habits, eCommerce growth was further accelerated by the global pandemic. But that growth comes with a price–an increased level of cyber attack.
According to research, 2020 saw a 20% growth in security incidents for 69% of the eCommerce businesses surveyed. According to monitoring of the deep web / darknet and hacker channels, 7.3% of posts were about the eCommerce industry, increasingly targeted due to the growth of the industry and the availability of new technologies, automated tools, and bot armies used by cyber criminals. These cyber attacks may lead to costly data breaches, not to mention potential violations of privacy and security laws (e.g. PCI DSS, GDPR, CCPA).
Trust is a foundational aspect of success on eCommerce apps & sites – trust that is undermined when the eCommerce site does not appear trustworthy or if there is a history of breached customer information. eCommerce web development takes a setback when security is threatened and it has to be addressedd seriously. One will have to integrate those efforts in a way that is visible to customers (e.g. eCommerce security badges, social proof).
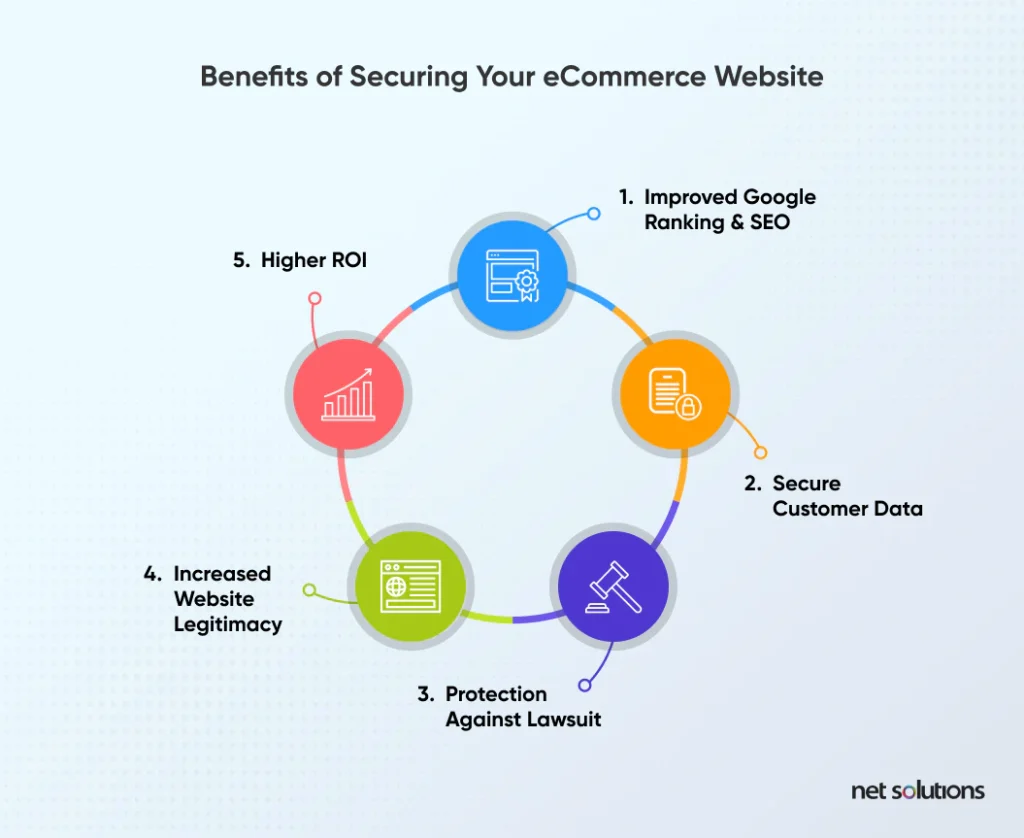
The remainder of this guide will outline the most common eCommerce security threats and a basic guide to how to make an eCommerce website secure.
Common eCommerce Security Threats
While there are many different kinds of cyber attacks, the attacks against eCommerce sites are usually targeted to steal customer data (personal or financial details), passwords, or cause disruption for financial gain. However, Ecommerce Challenges also include several kinds of financial fraud that are perpetuated by individuals as well as threat actors.
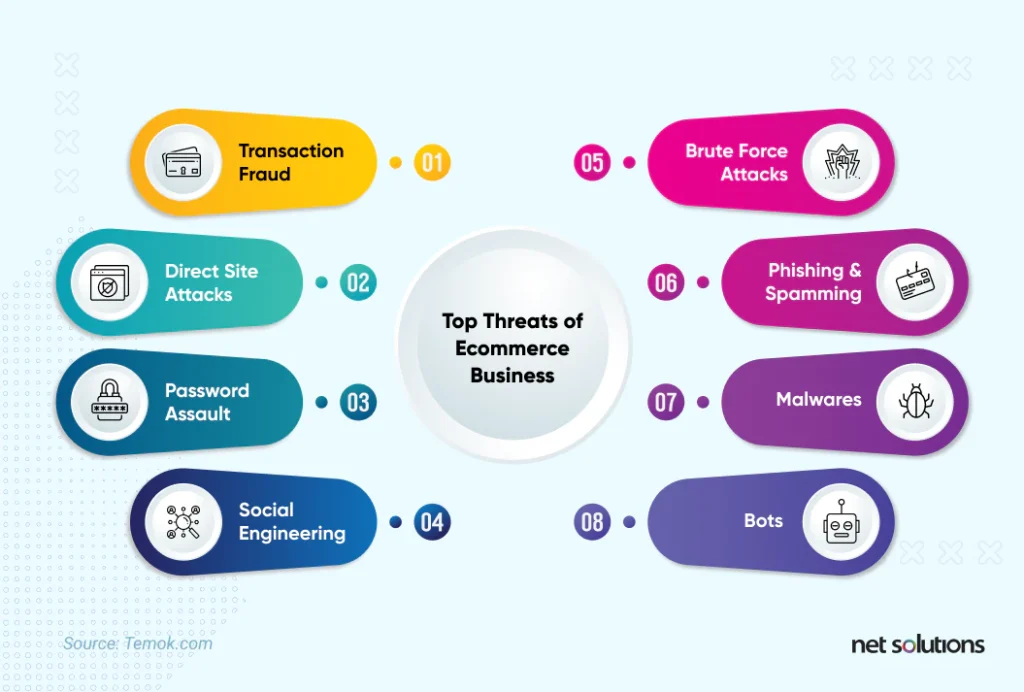
The most common eCommerce security threats are:
- Financial Fraud
eCommerce / payment / financial fraud is when any kind of
deception is conducted during a transaction for financial or personal gain.- Credit card frauds typically committed using a stolen credit cards.
- Unauthorized transactions through account takeover, cybercriminals make unauthorized purchases.
- Fake return & refund requests that involve various scams, including the intention to return stolen merchandise for cash, initiate a return without returning an item, or to lying to a credit card to dispute a valid transaction (chargeback
fraud)
- Social Engineering
A broad term that involves the use of some sort of deception or manipulation to get people to take an action (eg click a link in an email or on a blog
comment) or to divulge confidential information. Targets include consumers themselves (often pretending to be your brand) or employees, with the aim to gain access to
systems. - Phishing
Phishing attacks are designed to trick users into giving away
sensitive information (usually credentials) or to inadvertently download a virus or
malware designed to infiltrate systems or steal data. Such attacks most often come by
email, but can also come as text messages or even phone calls. - DDoS Attacks
These Dedicated Denial of Service (DDos) attacks send high
volumes of traffic that can make an eCommerce website slow and difficult to use.
Attackers use these attacks to damage reputation or for financial gain (blackmail). - Brute Force Attacks
The Brute Force Attack is an automated attack that uses
trial-and-error to guess possible passwords or passphrases to gain access, typically
targeting admin panels, but sometimes also targeting consumer accounts. - SQL Injections
SQL injection is a code injection technique that inserts code
into the SQL database to steal or wipe data from the database. - Cross-Site Scripting
(XSS)Threat actors inject malicious scripts into the browser code and
run at the client side to scrape user data. - E-Skimming
Inserting skimming code on eCommerce payment card processing
pages to capture financial and personal information. - Malware
Malware is designed to attack a website to steal data or send
spam from your domain or to provide for lateral activity to other areas of your data.- Trojan Horse is a kind of malware that misleads users and is downloaded to a
computer disguising as a legitimate piece of software. - Ransomware Ransomware is a kind of malware designed to steal and/or encrypt and lock
down data for the purposes of extortion.
- Trojan Horse is a kind of malware that misleads users and is downloaded to a
How to Secure Your eCommerce Website
The first step in protecting your eCommerce site is to recognize that its
needs are different from a standard website. eCommerce websites contain more valuable data,
including inventory, pricing, supply chain data, or sensitive user information (username and
passwords, contact details, financial information) that cybercriminals can exploit for
fraudulent transactions or sell on the black market.
- Choose a Secure eCommerce
PlatformLeading eCommerce
platform providers have proven capabilities to support a variety of industries
and Ecommerce
business models, with the proven ability to support performance, scalability – and security. Here are some of the leading secure eCommerce platforms:Magento
Trusted by over 250,000 active brands, and powering 12% of all eCommerce sites, Magento is a powerful PHP eCommerce platform – and the current Leader in the Gartner Magic Quadrant for Digital Commerce.
WooCommerce
WooCommerce sits as the second most popular eCommerce platform,
with a market share of 23.43%, operating as a free plugin built for
WordPress and designed to support small to large merchants who have some technical
knowledge.Shopify
As a leader in simplicity and user-friendly set-up, Shopify has
become a leader in the eCommerce
marketplace, with a wide range of tools and plugs to support customization.BigCommerce
For large, fast-growing businesses, BigCommerce has become a
platform of choice, with omnichannel
strategy and cross-channel selling and strong inventory management tools.Squarespace
The leading eCommerce provider in 2021 with a market share of 23.51%, Squarespace is known for its ability to
support creative designs, with modern templates for a more modern shopping aesthetic. - Switch to HTTPS

Most consumers now know the importance of https:// vs http:// and
know that a site with the padlock and the “s” for security is a genuine business that
has taken security seriously.An HTTPS website has received a security certificate that vouches
for the security of that website, protecting sensitive information on that connection
against eavesdroppers using the SSL/TLS protocols for encryption and
authentication. - Choose a Secure eCommerce
HostMany eCommerce platforms will offer hosting for customers with
off-site solutions such as Amazon Web Services or Google Cloud, but there
are also specialized web hosts that bundle eCommerce functionalities into their services
such as shopping cart software, payment processing, automated backups, caching, email
services, or data support. Look for a hosting provider that has:- SSL certificates
- DDoS protection
- Domain name privacy
- PCI Compliance
- Firewalls
- Spam filters
- Virus & malware detection and removal
- Encryption
- Automated backup
- Access controls that include SSH and strong authentication
- Strong customer support
- Network monitoring (and how customers are notified of potential threats)
- Physical security protections for servers (e.g. security cameras, gated access)
- Secure your Admin Area
Administrators have a privileged level of access to secure areas
such as the database or to controls on the eCommerce
website itself. To protect these sensitive servers and admin panels, consider:- Changing the default admin area
- Change the default administrator username and password
- Assign credentials by individual (not shared)
- Restricting access to the admin area (Permitting access to known IP addresses)
- Notify administrator on failed login attempts from unknown IP addresses
- Use strong authentication practices (difficult passwords, two-factor or multi-factor
authentication)
- Automate Data Backup
To protect against any kind of disruption, not just security, it is important to never lose customers or purchase information. Backups are the most obvious solution, but eCommerce websites cannot rely on web hosts to do this. The options are either manual – a time consuming process – or an automated backup solution that ideally runs the backup process on a different server (to eliminate performance disruption) and backs up any new changes in real-time.
- Secure Payment
GatewaysA payment gateway is a secure service to process credit card or
direct payments.When choosing a payment
gateway , make sure that it is:- Payment Card Industry Data Security Standard (PCI DDS) compliant – a standard that covers basic
security precautions for the storage and processing of credit card and cardholder
information. This is a requirement for all eCommerce websites. - Secured with SSL to encrypt information (see HTTPS section above)
- Leverages tokenization to store data away and assign it a key (in addition to
any other encryption or hashing that may protect the data) - International Organization for Standardization (ISO) certification – another
security standard that indicates the organization has conducted audits and proven
compliance to ensure the integrity and confidentiality of customer information (see
ISO
27001)
- Payment Card Industry Data Security Standard (PCI DDS) compliant – a standard that covers basic
- Data Collection
PracticesAlthough it is tempting to collect as much information as you can
about your customers to inform future marketing efforts, many privacy regulations now
are clear that data must be limited to only what is needed. Further, these same
regulations now include stipulations that consumers have a right to know what data is
being collected, to see that data, and to request it be removed (“the right to be
forgotten”). - Strong Authentication and
Access ControlsAuthentication (the process of verifying a user is who they say they are) is important for every user of the organization – but particularly for those with access to privileged information or systems. In larger organizations, it is also important to clearly specify the level of privilege – that each account only has access to the systems, software or records needed for that job, and no more.
Given the inherent vulnerability of passwords, 2-factor
authentication (2FA) and multi-factor authentication (MFA) involve more than one step in
authenticating a user is who they say they are. Both 2FA and MFA involve some
combination of something a user knows (e.g. password), something a user has (e.g.
one-time passcode), or something a user is (e.g. biometric data). For larger
organizations, access control solutions such as IAM and PAM can help address security
concerns. - Enforce Strong Passwords for
CustomersStrong password hygiene is the first step in improving access to
your eCommerce website, which we can achieve by mandating complex passwords. However,
passwords continue to remain a weak method of authentication that the threats we
mentioned above can easily exploit. Hence, it is recommended to implement 2FA or MFA for
consumers as well as internal employees. - Implement Website Hardening
MeasuresTo reduce brute-force attacks against the site, whether on
consumer logins or for employee logins, it is important to limit login attempts. This
option may be available in the eCommerce platform, via a plugin, or as a third-party
solution. - Create Security Policies
& ProceduresSecurity best practices always involve a combination of
technology alongside improved policies and processes. These policies apply to everyone
at work on the eCommerce site, from the customer service desk to the IT desk. This
includes:- Clearly articulated policy on safe practices such as what to do if you suspect
fraud, data handling processes (i.e. never copying or sending data, even to
yourself), not sharing passwords, patching - Have a clear privacy policy for consumer information
- Staff training, provided on an ongoing basis, on topics such as phishing attacks,
password hygiene, compliance - Regularly review third-party plugins and solutions in your store to ensure they are
being updated by the partner and that they are patched to the latest version. Remove
unused plugins.
- Clearly articulated policy on safe practices such as what to do if you suspect
- Have Multi-Layered
SecurityTo mirror the policies and procedures, eCommerce owners must utilize several different technological barriers to improve security. Multi-layered security is the concept of creating a defense in depth – that if one layer fails, another will still be there. The multi-layer concept also ensures defense against many kinds of channels of attack, including email and phishing.
- Web Application Firewall
A protective barrier between the Internet and the eCommerce website - Content Delivery Network
A content delivery network (CDN) helps ensure fast delivery of the website through
caching, but can also provide DDoS mitigation, improvements to security
certificates, and other security features. - Geolocation Anti-Fraud Software
Geolocation data can help combat the more sophisticated attacks on eCommerce,
finding irregularities in the IP address or origin of the data and helping to verify
cardholder details against transactions to flag for fraud. - Threat detection & monitoring software
These tools help detect and assess vulnerabilities to eCommerce websites, networks
and databases and provide ongoing monitoring of website activity and logins. There
are many kinds of third-party monitoring tools available including analysis of disk
space, CPU usage, response time, change detection, service uptime, responsiveness,
broken links, as well as tools that can perform vulnerability assessments and
penetration testing.
- Web Application Firewall
- Keep Your system patched &
updatedRegularly updating systems and applications that we use in the
eCommerce site is probably the most important step to maintain security (as well as
performance!). These updates contain patches to known security vulnerabilities. In fact,
57% of cyberattack victims report the breaches could have been
prevented with an available patch.
Your Trusted eCommerce Services Partner
In the present environment when regulations are continuously evolving and
new security threats are emerging, it’s essential to take necessary measures to safeguard your
Ecommerce website. You may feel that you can handle the security of your ecommerce website on
your own or offload these responsibilities to your platform provider, it’s not going to be easy.
Hence, it’s best to have a reliable ecommerce services partner by your side.
If you are looking for someone to help you in auditing your eCommerce website for security, or building a new eCommerce store – our experts can you help provide a strategy to create a robust, scalable, and secure site to sell your products and services.
Frequently Asked Questions
1.What is an eCommerce Security Badge?
A trust badge helps to demonstrate that a website is legitimate and uses
vetted third-party service providers. Although the “Guaranteed Safe Checkout” badge denotes that
an SSL is used during checkout, some eCommerce websites also add money back guarantee and other
service-related badges.
2.How do I know if my website is secure?
Although the eCommerce security best practices offer great insight into
how to become secure, the first step is getting a baseline. There are scanning tools available
(e.g. FreeScan and other great options) that provide an overview of current security posture,
although these are often very surface level recommendations. If you don’t know where to begin, a
security audit by a trusted partner is a great first step.
SHARE THIS POST
Table of Contents
Related Resources
- eCommerce App Development Cost: Budgeting In-Depth Guide
- 13 Differences Between B2B and B2C eCommerce Websites
- Top 10 eCommerce Challenges and Easy Ways to Overcome Them
- 3 Types of eCommerce Business Models That Work in 2024
- eCommerce for Business: Is eCommerce Applicable for All Business Types
- eCommerce Customer Journey Mapping - The Secret to Higher Conversion Rates
- What is Headless Commerce? The Ultimate Guide
- Top 15 eCommerce KPIs to Track the Performance of Your Online Business
- Why Your Business Needs a Mobile eCommerce App
- Omnichannel Retail Strategy: A Comprehensive Guide
- Omnichannel vs Multichannel Retailing: The Complete Guide
- What is eCommerce Order Fulfilment? (And 6 Steps to Improve the Process)
- PCI Compliance: Everything You Need To Know
- The BEST Guide to eCommerce Personalization
- 12 Essential Factors for Choosing the Best eCommerce Platform
- The Ultimate Guide to Product Information Management (PIM) Systems for Ecommerce
- What is a Product Recommendation Engine (And How it Helps Boost Sales)
- eCommerce Replatforming: Challenges, Benefits, and Best Practices
- Top 13 eCommerce Trends in 2024
- How Voice Search will Transform the Future of eCommerce
- What is Web Accessibility (And Why it Matters for Your eCommerce Business)



