Summary: Database security affects all of us, whether or not we know it. Learn why it is important, the basics of database security, common vulnerabilities and best practices to fend off any attacks.
A database is designed to store, organize, manage, and support electronic access to a collection of data, much of which is confidential or proprietary, sensitive, or protected in some way by industry, state, federal, or global regulations. That data has value to cybercriminals, either for the purpose of financial gain, disruption, or cyber espionage.
With a 50% increase in cyberattacks per week compared with the previous year, it is more important than ever before to institute programs to protect databases against intrusion, misuse, or damage.
What is Database Security?
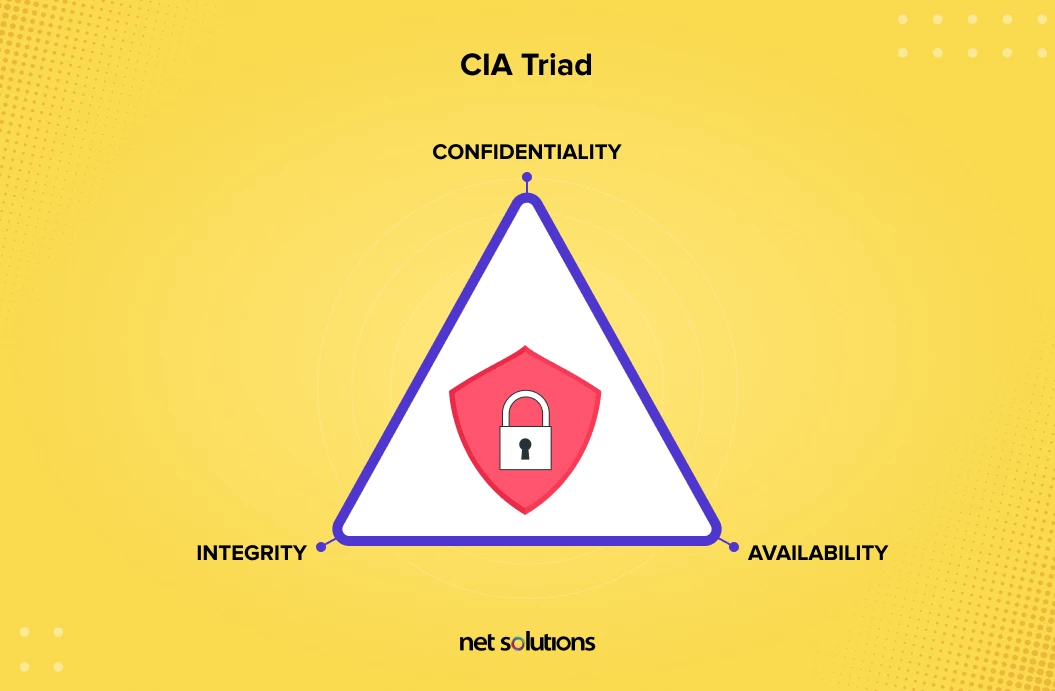
Database security refers to the controls, tools, policies and other measures designed to preserve the confidentiality, integrity, and availability of data, as well as the data management system and the applications that access it.
What Does Database Security Include?
Database security programs are designed to protect all aspects of the data and its broader ecosystem, including:
- The database server (physical, virtual, underlying hardware)
- Data in the database
- The database management system (DBMS)
- Applications that access the database
- The computing & network infrastructure used to access the database
Why is Database Security Important?
The top reason cited for the importance of database security is to reduce the risk of a data breach. According to recent data, the average cost of a data breach is now at $4.24 million, a huge 10% increase over the previous year – and even higher where remote work was a factor. However, there are many reasons for database security, including:
- Protection of Intellectual Property (IP) against exfiltration or loss (e.g. hardware failure), which can impact the ability to compete.
- Prevent data breaches, which carry a high cost both in actual dollars (regulatory compliance fines, legal fees, breach notification costs) we well as brand reputation.
- Business continuity due to a loss of IP or high breach costs. Many small-to-medium sized businesses would close if they experienced a breach.
- Regulatory compliance requirements to maintain data integrity and support a user’s right to be forgotten.
Businesses That Need Database Security The Most
Cybercrime does not discriminate, attacking all industries and businesses of all sizes. While that is true, some industries are more heavily targeted than others – industries whose data may be higher in value on the black market, are a target of cyber espionage, or whose protections may be perceived as weaker.
1. Healthcare
Patient information is more valuable on the black market, at least 10 times more valuable than credit card data, with healthcare the most highly targeted industry for cyber attack. A complex mix of legacy and new medical devices, combined with the trends of mergers & acquisitions and the complexities of managing data access for rotating and contract staff, increases the risk that gaps will be overlooked.
2. Government & Critical Infrastructure
During the last two years, there has been a trend toward attacks perpetrated by nation state attackers who are motivated by financial gain as well as a desire to disrupt and destroy or take part in cyber espionage (spying) activities. In 2020, 13% of malicious breaches were caused by nation state attackers.
3. Financial Services
Behind healthcare, financial services face one of the highest costs of data breach and one of the highest rates of attack. In fact, 28% of attacks on finance were server access attacks.
4. Retail & eCommerce
At least 10.2% of all attacks target the retail industry due to the high value financial and personal details stored in databases.
Database Security Threats and Vulnerabilities
The most common database security vulnerabilities, threats and challenges include:
1. Insider Threats
They are risks from those with inside access to systems and data, which could include current employees as well as past employees (with retained access) or third-party partners or contractors. Insider threats have risen 44% in the past two years with a cost per incident up to $15.38 million. Malicious insider threats are also increasingly targeting database backups.
Insider threats can be both malicious (from those who intend harm for profit or revenge) and negligent (from those who make mistakes that introduce risk). The use of compromised credentials also constitutes an insider threat, with an outside attacker gaining access to credentials through phishing or compromise of the credential database.
2. Human Error
Human error is the leading cause of serious data breaches, tied back to 84% of security incidents, meriting special attention. The most common human errors include: clicking phishing links, poor password hygiene, password sharing, ignored patching, and the unauthorized exfiltration of secure data to another source (e.g. cloud application, email). Human error can also compromise physical security, e.g. allowing someone to walk into a secure area without authentication.
3. Cyber Attacks
Cyber attacks come in many forms, but the most common attacks and exploitations in database security include:
A. Database software vulnerabilities
Vulnerabilities are common to all software, including database management platforms, networks, or applications used to access these systems. Without regular patching, these vulnerabilities leave systems open to attack.
B. SQL/NoSQL injection attacks
All database systems are vulnerable to this kind of attack, which allows attackers to execute commands in the database or to inject code into commands for databases.
C. Denial of service (DoS/DDoS) attacks
Attacks shut down a machine or network, making it impossible to access the database. The most common DoS attack is a buffer overflow attack, which sends more traffic to the system than it is designed to handle.
D. Malware
Malicious software (malware) is software that is designed to intrude into target systems to steal data, disrupt or damage systems. The most common dangerous types of malware are ransomware (where criminals encrypt information and demand payout) or zero-day attacks, which exploits database software vulnerabilities before the vendor has become aware of it.
4. IT Environment Pressures
The changing IT environment is putting pressure on existing databases as well as database security practices and tools, not all of which are keeping pace. Some of the top pressures on IT environments include:
A. Data volume
The growth in ‘big data’ creates new pressures on how data is captured, stored, processed, and backed up. Not all systems and processes are scaling well, leading to slow systems, risks, and increasing errors.
B. Distributed infrastructure
As organizations increasingly adopt cloud infrastructure and the microservice architecture, the database security challenges become exponentially more complex.
C. Regulatory requirements
The regulatory environment is changing rapidly at the state, federal, industry and global level, now requiring more from database security (e.g. data integrity, right to be forgotten), which some systems cannot handle.
D. IT skill shortage
The IT skill shortage in the US, particularly in cybersecurity, makes it difficult for many organizations to keep up with the changing demands on database security.
5. Design & Deployment Failures
Deployment is a critical point for database security. Although many organizations will conduct functional testing to ensure the database will perform as expected, these tests will fail to identify if the database will do more than expected (negative impact), has flaws in chosen features or controls, or if the database is missing critical protections that could impact security.
Database Security Control Types
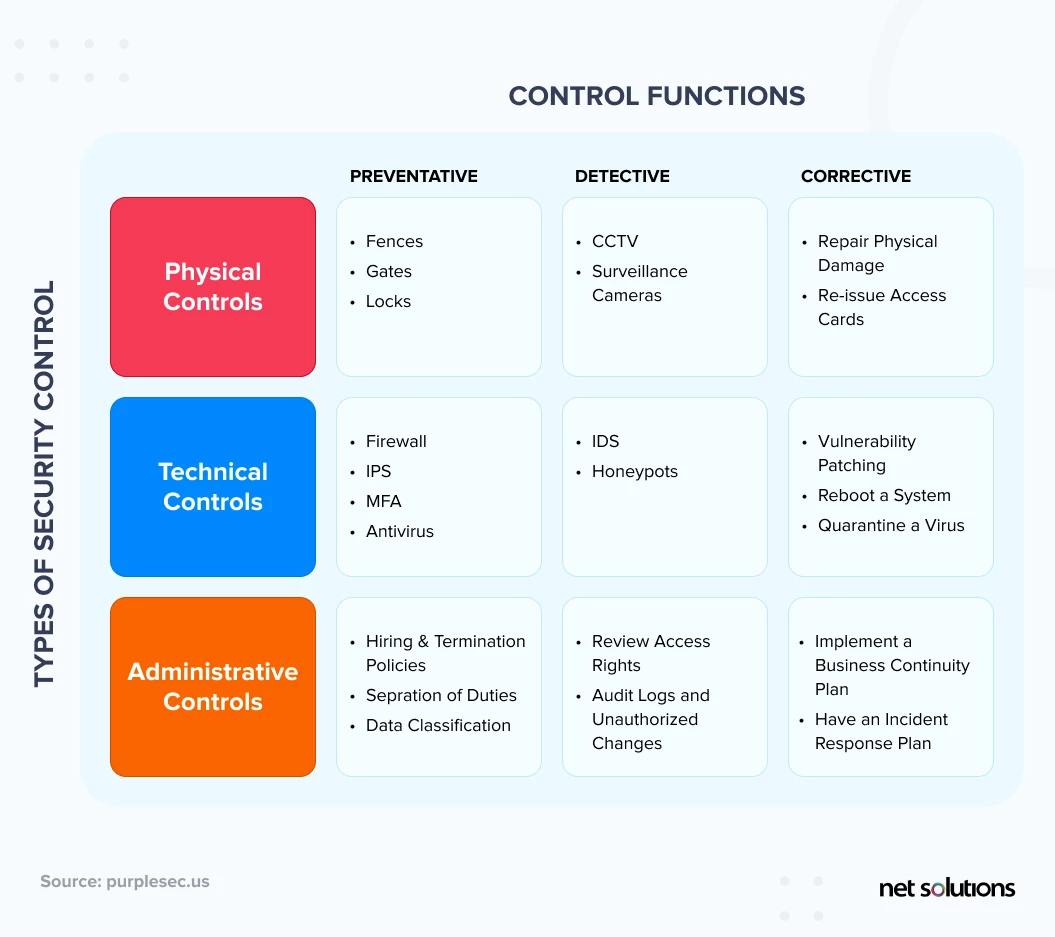
Many of the above vulnerabilities and challenges can be improved through better database security controls. These controls are designed to either prevent, detect, or remediate / reduce the impact of a security intrusion or loss of availability.
There are three different types or categories of controls used in database security:
- Physical controls
- Technical controls
- Procedural / administrative controls
Database Security Best Practices
Within the three types of database security controls (physical, technical, administrative), there are many specific layers. These layers help inform the design, deployment, and ongoing use of the database within a specific IT environment.
When evaluating database security, consider the following best practices:
1. Physical Security
Ensure the database server is protected, whether on-site or in a cloud data center, by physical access measures (e.g. card or hardware-based authentication protocols) in a facility that is adequately monitored and climate-controlled. For those using web hosting, due diligence should be done to ensure database security.
2. Technical Controls
Many vulnerabilities to database security can be addressed through improved database design. In this design phase, choices can be made to minimize development risks, including:
- Separate the web server from the database server to ensure that compromises at the web level do not impact the database server(s).
- Use implementation testing to ensures to testing moves beyond functional testing to avoid deployment failures.
- Separate each database server to provide greater redundancy and isolate any potential exposures to data.
- Limit features as hackers are increasingly exploiting standard database features to run code that compromises a system. By limiting features, this reduces the potential attack surface.
- Use web application and database firewalls to prevent outbound connections.
- Set up a HTTPS proxy server.
- Avoid using default network ports.
- Choose security tools such as anti-virus, password scanners, data masking, network auditing, SQL injection testers and scanners, vulnerability scans, and more (see below section).
- Disable public network access and instead use a gateway server.
- Ensure ongoing testing of all applications and web servers that interact with the database.
- Ensure the database management software is up to date before implementation, with a plan for regular patching (see section below).
3. Patching
One of the biggest areas of vulnerability in any database system is a lack of effective patch management of database servers and applications that connect to the network as new vulnerabilities are discovered regularly. Further, many patches address stability issues, helping address the integrity and availability of the database system.
4. Access Controls & Authentication
Access controls determine who gets access to a system and in what capacity – to read, create, update, or delete resources in the database system. Authentication is the process of verifying a user is who they say they are.
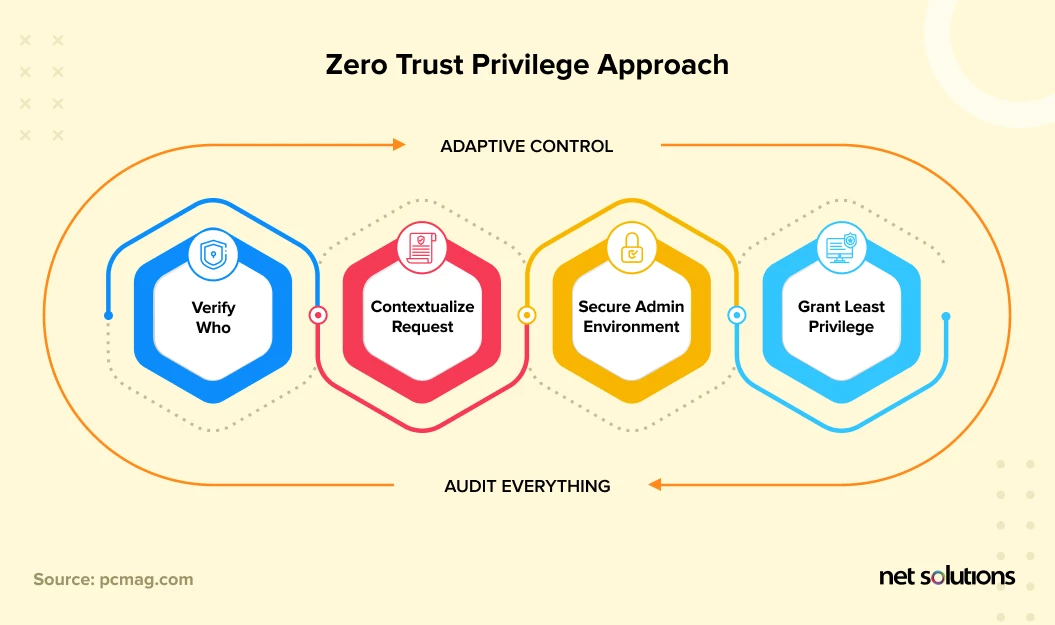
For database security, it is important to actively manage access controls with the concept of “least privilege,” assigning the minimum number of permissions necessary for users to do their jobs and separating admin account access, and “zero trust”, to always verify users are who they say they are. Database security programs must regularly audit user access, review onboarding and offboarding processes, and consider more stringent authentication for privileged users.
Access Controls & Authentication Checklist:
- Set up basic controls for access management
- Set up policies that govern administrative or privileged access to the database (to install, change, configure, delete or otherwise manage the database)
- Consider higher level controls for privileged use / privileged users (IAM, PAM)
- Determine authentication factor(s) and any enforcement needed (e.g. password strength, account lock settings, encryption of stored passwords)
- Set up regular review to enforce least privilege access and remove unused accounts regularly
5. Monitoring & Auditing
Database security requires regular monitoring and auditing to ensure ongoing compliance. Regular intelligence gathering will include ways to monitor activity and provide alerts for anything suspicious:
- Real-time database monitoring
- Activity logs for all logins and operations
- Threat intelligence / anomaly detection
- Vulnerability assessments
- Data intelligence tools (e.g. sensitive data recovery)
- Regular audits
6. Encrypt Data
All data in the database, and in backups, should be encrypted to provide protection for both in transit and at rest data. Database encryption is a process of using an algorithm to transform text into “cipher text” that becomes unreadable without being decrypted. The goal of encryption is to both protect the data and to make the database less attractive since the data would become meaningless to cyber criminals.
There are many different approaches and technologies for database encryption. Pay particular attention to key management, which is often a flaw in many encryption programs.
7. Integrity Controls
Database integrity controls help ensure the accuracy and consistency of data stored in the database. Data integrity controls are designed to reduce human error, introduce resilience from outages, hardware failure, transfer errors, or disruptions from hackers. Data integrity is a critical component of regulatory compliance (e.g. GDPR).
Consider common database integrity controls and processes, including:
- User access controls and authentication
- Data validation (at input and in use)
- Removal of duplicate data
- Backup and logging processes
- Regular audits
- Error detection software
Database Security Tools and Platforms
To support the above best practices, there are a number of security vendors that offer individual tools or all-in-one platform capabilities in the following tools and platforms:
1. Discovery Tools
Discovery tools will scan systems with various purposes: to look for vulnerabilities, audit network and security, uncover configuration mistakes, identify access control issues, find missing patches, identify sensitive data or data leakage, identify weak passwords, and more.
2. Database Activity Monitoring
These tools help detect, respond to and protect against cyber attacks through data discovery (find all the places where data lives), monitor activity on the database (from people and applications), and provide analytics, and support response and auditing activities.
3. Encryption
There are many tools and platforms that help support encryption and tokenization. You can use them to safeguard the information you’ve saved in databases and ensure it doesn’t fall in wrong hands.
4. Access Controls & Authentication
There are many third-party services that support access controls the management of privilege, including IAM and PAM systems, as well as improved authentication options such as OTP or hardware or passwordless authentication for the most privileged users or data.
5. Analytics
The ideal database security configuration will include the use of a tool or platform that can provide data analysis from the entire system to help get a more complete picture of risk, optimization, and reporting capabilities.
Conclusion
Today’s digital world relies heavily on databases, so it is important to protect these valuable assets against attack and to maintain the integrity and availability of data at all times. However, database security has many moving pieces and, as addressed earlier, many organizations lack the adequate internal skills to stay on top of the changing risk landscape.
Whether you are migrating to a new cloud environment or are looking for an audit or optimization of your database security posture, Net Solutions has expert database developers to take a deep dive into your needs.
Frequently Asked Questions
There are four levels of database security: the security level, database level, the access level, and the perimeter level.
- The Security level deals with database security solutions.
- The database level involves tokenization, masking, and encryption.
- Access control lists and permissions are the part of the access level.
- The permeter level includes virtual private network and firewalls
Here are some precautionary measures you can follow to safeguard your database from SQL injection attacts:
- Keep your database server up to date with latest security patches from vendors.
- Use the principle of least privilege to ensure you don’t give insert, update, or delete permissions to just about anyone.
- Avoid using shared database accounts between different websites/web applications
- Never forget to validate user-supplied before using it. They often induce most common risks of SQL injection attacks.
- Regularly scan your database for any potential issues from time to time.
The different types of database security tests are:
- Penetration Testing: Intentionally attacking a system to discover security loopholes.
- Risk Assessment: Conducting a risk assessment to determine the levels of risks involved with your database.
- Password Cracking: Using password-cracking tools to see if your passwords can be hacked or not.
- Security Audit: Conducting security audits to see if the organization is following security standards or not.
DbUnit, JDBC (Java Database Delta Testing), DbStress, NoSQLMap, NoSQLUnit,sqlmap, and Tsung are some popular database security testing tools.
Database hardening refers to the process of analyzing your database for security vulnerabilities and fix them using recommended best security practices.