We’ve all heard the horror stories—Microsoft, Yahoo, Facebook, Equifax, and other massive organizations have experienced major data breaches despite well-developed cybersecurity practices. These breaches exposed the data of billions of users to cybercriminals, impacting brand reputations and the trust users placed in these institutions.
No network is risk-free, but failing to adhere to cybersecurity compliance requirements in the countries and industries you serve can result in major fines and even criminal liability if your practices are deemed negligent. That’s why cybersecurity compliance is so vital.
Users rightly expect businesses to be good stewards of their data, and security regulations are set in place to support that very principle. This blog post will help guide you in your efforts to remain compliant and keep your customers’ data safe.
Compliance and Security in Outsourcing 101
IT outsourcing has become a permanent fixture in the modern business world, with 99% of Fortune 500 companies outsourcing at least some portion of their software development needs to overseas partners. Naturally, this raises questions about security and compliance.
The truth is that outsourcing software development to any outside firm, whether they’re located across the street or around the world, poses risks. These risks are manageable if you choose the right partners, and the rewards are many, but we would be remiss if we pretended the risks didn’t exist.
Many outsourcing partners follow strict protocols and cybersecurity best practices, but it’s vital to properly vet them and ensure they understand compliance requirements in the countries, regions, and industries you serve.
A new software development outsourcing firm may have excellent developers and project managers on staff, but without proven experience in your field, it’s difficult to know whether they truly understand the key compliance and security challenges you face.
Choosing the wrong outsourcing partner could pose security and compliance risks due to:
- Poor communication
- Substandard protocols for handling sensitive information
- Poor cybersecurity practices
- Inexperience or lack of knowledge surrounding rules and regulations in your country and/or industry
You may even encounter an unscrupulous outsourcing partner who compromises your data intentionally—but this is highly unlikely if you choose an experienced firm that has been in the business for 10+ years. If you go with a rookie, it’s more of a concern.
We don’t mention any of this to scare you away from outsourcing. After all, we’re an IT outsourcing firm that has been serving our clients for nearly a quarter century without incident. We just think it’s important to understand any and all potential risks before choosing a partner.
Read on to learn about common compliance and security concerns and best practices for mitigating those risks when seeking outside support to handle your IT needs.
Key Compliance and Security Concerns to Manage
Security requirements differ from one industry to the next, and government regulation exists to address those challenges in key industries throughout different regions and countries.
For example, healthcare companies operating in the United States are bound by the Health Insurance Portability and Accountability Act (HIPAA), which prioritizes patient privacy. Another massive regulatory move occurred when the European Union passed the General Data Protection Regulation (GDPR), which impacts anyone collecting data or distributing emails to clients or prospects living within the EU.
It’s vital to choose a partner who has experience adapting to requirements and is willing to learn about your industry’s needs. Here are a few general themes these regulations touch. Be sure that any potential partner understands how to address them.
Data Protection and Privacy
Protecting customer data is at the core of cybersecurity, and it’s the essence of GDPR and other data protection requirements. Keeping your customers’ data secure is not only a legal requirement in many jurisdictions, it’s the only ethical way to run a business.
Data protection and privacy means:
- Keeping your customers’ passwords, credit card information, and any personal data (such as health records) safe from both external threats and internal employees who have no business looking at the data
- Accurate record-keeping to secure the integrity of your system
- Accountability systems that clearly identify who is responsible for maintaining customer privacy
- Data minimization to reduce the risk of exposure
- Proper backups to reduce the risk of data loss
- Regular purging of data that your organization no longer needs to store
This just scratches the surface, but it’s a good start. Anytime you work with an outside partner, make sure they have systems in place to handle data privacy and protection, including those items listed above.
Intellectual Property (IP) Protection
Protecting both your company’s and your clients’ intellectual property is an important element of security and compliance. Negligently exposing IP could have serious business and legal consequences.
When working with an outsider, be sure they follow established protocols for securing all sensitive data, including IP belonging to your company and your clients. Needless to say, you’ll also want to be sure they’ve signed legally binding non-disclosure agreements as well.
Regulatory Adherence
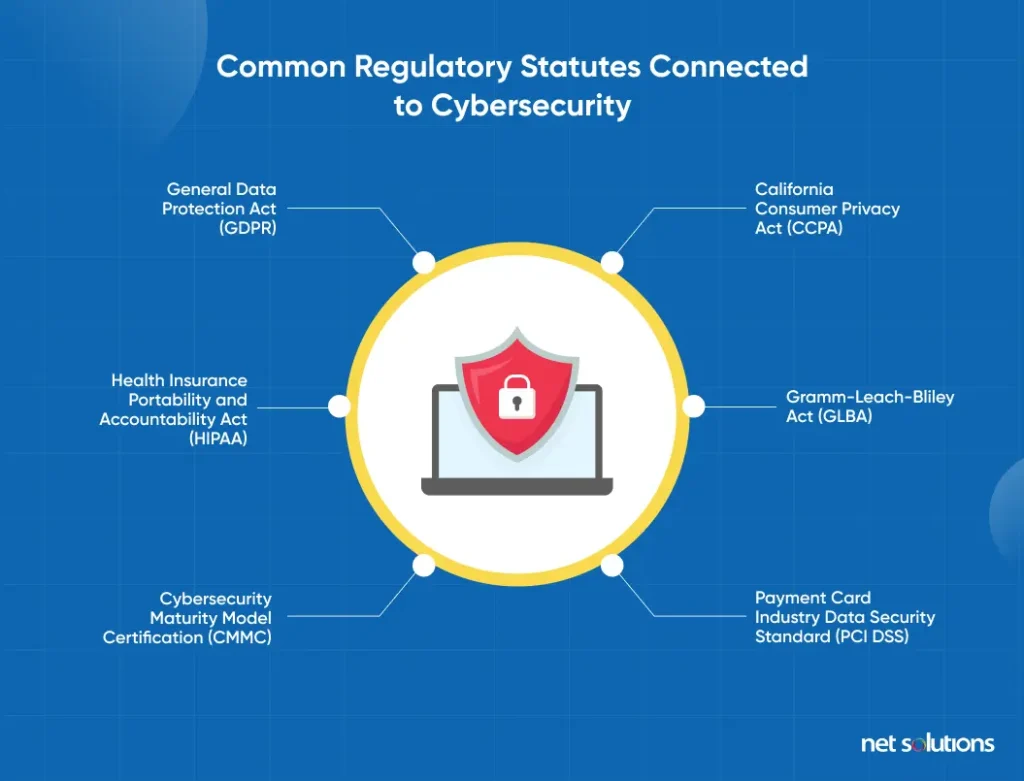
As we mentioned above, the world is filled with regulatory requirements that impact different regions and industries. Here are some examples of common regulatory statutes connected to cybersecurity, but this is by no means a comprehensive list.
- General Data Protection Act (GDPR): Deals with protecting customer data and impacts anyone who handles data for EU residents.
- California Consumer Privacy Act (CCPA): Protects customer data and affects anyone who deals with the data of California residents.
- Health Insurance Portability and Accountability Act (HIPAA): Affects anyone handling medical data of U.S. citizens and residents.
- Gramm-Leach-Bliley Act (GLBA): Regulates data handling for financial institutions within the United States.
- Cybersecurity Maturity Model Certification (CMMC): Impacts defense contractors within the U.S., requiring strict adherence to data protection to safeguard national security interests.
- Payment Card Industry Data Security Standard (PCI DSS): Impacts eCommerce retailers and anyone who handles credit card transactions within the U.S.
Note: Net Solutions is a certified Level 1 PCI DSS Services Provider
Again, this is just a short list of different types of regulations you might contend with—designed to give you a sense of the inherent complexities of the international regulatory environment.
An experienced, professional outsourcing partner is prepared to learn about these requirements and build software systems that adhere to whatever your business requires based on your region and industry.
10 Best Practices for Mitigating Security Risks
What can you do to reduce your risk of security breaches and remain in compliance based on your industry and the regions you serve? While there are no guarantees, the following 10 best practices will help you mitigate risk when working with an outsourcing partner.
Vet potential vendors
The most important step you can take when working with an outsourcing firm, regardless of where they are located, is to thoroughly evaluate potential vendors.
There are plenty of highly professional outsourcing firms with strong track records and solid processes in place for maintaining privacy, but you need to separate them from incompetent or unscrupulous firms. Here’s what you need to look for in a vendor.
When hiring an outsourcing partner, ask tough questions about their:
- Track record: Do they have a long history of working with enterprises and developing systems that adhere to their specific regulations?
- Security protocols and processes: What systems do they have in place to protect their clients’ data?
- Compliance history: Who have they worked with that required strict adherence to cybersecurity regulations? Do they have any history of security failures?
- Reputation: What are their clients saying about them? Scour their reviews on websites like Clutch.co, which evaluate outsourcing partners. If they don’t have any reviews, you might want to work with a more established provider.
When vetting providers, look for important certifications, such as the PCI DSS Level 1 Service Provider Certification, which Net Solutions received in 2023. Our PCI DSS expertise came into play when we built a powerful eCommerce website for Euro Car Parts, ensuring their online store could handle secure credit card processing.
Additionally, our Trusted Information Security Assessment Exchange (TISAX) designation helped us gain the trust of Porsche, another large client. This let them know that we adhere to the auto industry’s stringent security exchange standards. Don’t be afraid to ask for similar certifications and experience related to your industry.
If you do your due diligence when vetting potential vendors, you can easily find an outsourcing partner that is competent, and responsible, and will do everything within their power to keep your data secure (and your business compliant).
Encourage open communication and collaboration
Once you find a partner you can trust, clear communication is key to success because even the most talented, responsible teams can fall short if communication proves inadequate.
The following guidelines will help you establish clear communication, which will impact every element of your success—from compliance to the functionality of the software products you create together.
- Strong language skills: Work with a team that speaks your operating language with a high level of fluency
- Regular meetings and updates: Meet regularly with project managers
- Transparency: Ensure your team is clear about any challenges at every stage of the development process
- Agile & DevOps methodologies: Even if you’re not taking an Agile and DevOps approach to your projects, the principles of regular communication central to these methodologies will help ensure clear communication
Using project management tools like JIRA and roadmapping tools like Aha! can give everyone a bird’s-eye view of the project and help spot gaps in communication before they become an issue.
Make clear contractual agreements
Clear contracts make for ideal business arrangements. Even when both parties enter into an agreement with the best of intentions, well-written, legally binding contracts—from Service Level Agreements (SLAs) to Non-Disclosure Agreements (NDAs)—protect everyone’s interests.
When it comes to meeting cybersecurity and compliance requirements, your contracts should include detailed clauses that protect your interests, including:
- Data protection clauses that outline the efforts the provider will take to protect your (and your clients’) data
- Fully outlined security protocols that the vendor will follow
- Responsibilities in case of a security breach
As always, run everything through your attorneys before signing on the dotted line.
Integrate security practices at every stage of software development
We tend to think of security coming into play post-deployment since bad actors will search for security holes once a software system is live. However, security best practices come into play at every stage in the development process. After all, human beings are involved in every step, and every human (and each transfer of data) represents a potential point of failure.
Here’s a brief introduction to how security comes into play at each stage.
- Planning introduces the exchange of vital information, including company secrets. Be sure to use controlled documentation to protect company secrets.
- Design also involves the exchange of sensitive information. As designers interact with developers and project managers, they must do so on secure systems.
- Development includes the exchange of vital information, especially when using highly collaborative systems like Continuous Integration/Continuous Development (CI/CD). Developers must follow established procedures to limit exposure.
- Testing also involves a large transfer of information, especially when you’re working with offsite testing teams. Transfer that data through secure systems.
- Deployment often involves introducing new data centers and data sources, and bad actors may try to exploit weaknesses during periods of transition.
Proper planning, with professional guidance and a DevSecOps approach to security, can help mitigate risks by integrating security at every element of your software development framework.
Establish responsibilities to boost ownership
Assigning ownership is key to cybersecurity when it comes to software development. In other words, different roles must own specific tasks related to security threats. Without ownership, it’s easy to “pass the buck” and assume someone else will take care of managing risks for a given element of the process.
Since there are different components to any system, different owners will be assigned to each component (e.g., data transfer, encrypted communication, deployment). Ultimately, however, someone must oversee the overall security strategy. Ideally, that will be someone with years of experience managing security risks.
Determine quality standards and KPIs
When it comes to cybersecurity, it’s impossible to manage what you don’t measure. That’s where Key Performance Indicators (KPIs) come into play—metrics that clearly illustrate your success (or lack thereof). KPIs for cybersecurity might include:
- Code coverage
- Vulnerability
- Bug fix rates
- Anything else related to optimizing security
At Net Solutions, we take Quality Assurance (QA) seriously, especially as it relates to cybersecurity. We use a DevSecOps approach that is data-driven to mitigate security risks and double down on what works.
Run regular audits and assessments
Regular cybersecurity audits help you assess weaknesses in your efforts and address them. Common audits and tests you can run include:
- Penetration testing
- Code reviews
- Configuration audits
- Compliance audits
- Risk assessment audits
Continuous monitoring will give you a realistic look at your vulnerabilities, compliance gaps, and other areas of concern so you can address them.
Implement strong authentication mechanisms
No system is truly secure without carefully considered authentication systems. In fact, certain industries require extra authentication steps, such as Multi-Factor Authentication (MFA), in order to remain in compliance with legal statutes.
MFA is a process we’re all familiar with at this point, even if we don’t know it by name. When we log into a banking or credit card account from an unknown device or WiFi network, we’re prompted to enter a code sent via text to our cell phones or sent to an email address.
The U.S. Federal Trade Commission (FTC) has begun requiring Multi-Factor Identification when customers log into their accounts from unknown devices. And while MFA is not currently required for HIPAA compliance, it’s helpful in protecting patient data.
Have an incident response plan in place
Be prepared in case you experience a data breach or some other cybersecurity incident. Come up with a clear plan to deal with:
- Detection of the problem
- Containment of the threat
- Eradication of the threat
- Recovery to restore data loss and mitigate damage
Clearly outline the proper procedure in your response plan, noting communication channels, roles played, and the responsibilities of everyone involved.
Emphasize employee training
It’s important to educate your entire company, not just your IT staff, on the importance of security procedures. In fact, while IT professionals are often aware of how to spot and deal with threats, the average employee may have no idea that something is suspicious.
Educate your staff on common threats, such as phishing attempts. Encourage them to look carefully at email addresses, never give out passwords, avoid clicking on suspicious links, and handle sensitive data with the utmost care.
Navigate Compliance and Security with a Trusted Partner
When working with an outsourcing partner, it’s essential to choose someone with a proven track record serving large enterprises with strong security needs—especially a team that has managed a complex regulatory environment.
Net Solutions has more than two decades of experience working with well-known organizations in a variety of sectors, from finance to healthcare. We’ve also developed software and managed risks for household names like the Harvard Business Review and IMG.
We specialize in digital transformation and software development, providing staff augmentation as well as full-scale, end-to-end efforts that spearhead every element of a company’s IT initiatives if that’s what they require.





